As corporate espionage and data theft evolve increasingly sophisticated tactics, inadequate As corporate espionage and data theft evolve increasingly sophisticated tactics, inadequate protection of sensitive files renders organizations susceptible to intellectual property loss, compliance fines, and privacy violations. Determined hackers, spies from rival companies or governments, and malicious insiders represent existential data security threats often overlooked as hype until disaster strikes. Within intricate digital jungles lurk predators awaiting easy prey while business leaders and employees generally have more pressing priorities. Luckily certain encryption tools provide robust defenses, acting as steel vaults guarding secrets, financials, personally identifiable information, and other confidential data from stealthy marauders. This article outlines the capabilities of top 10 encryption software facilitating secure collaboration across globally dispersed teams operating in dynamic regulatory environments. Leaders must implement layered solutions encompassing device and network protections alongside trustworthy end-to-end encryption, multi-factor authentication, strict permissions, and activity logging supporting real-time alerts and audits.
1. EaseUs LockMyFile
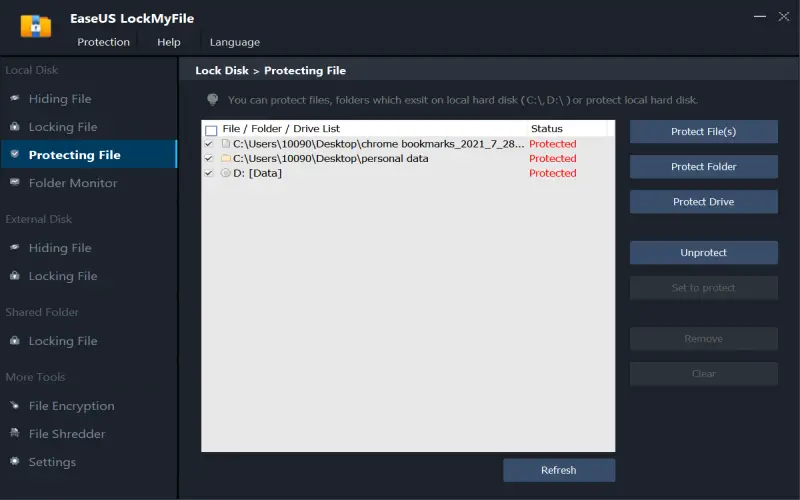
A file-focused tool providing accessible functionality through the straightforward interface for efficiently protecting documents, images, videos, and archives across Windows environments with military-grade AES 256-bit encryption and hash checksum validation. Standout features include encrypted MySQL database backups plus disaster recovery tools like incremental backup supporting versioning. Light-weight agent facilitates seamless collaboration, remote wipe capability thwarts data exposure if devices get lost or stolen. Encrypted archives remain portable across platforms with included MacOS and iOS decryption apps. Centrally managed through a browser-based console enabling administrators to define granular folder access policies and permissions, and reset user passwords.
2. BitLocker
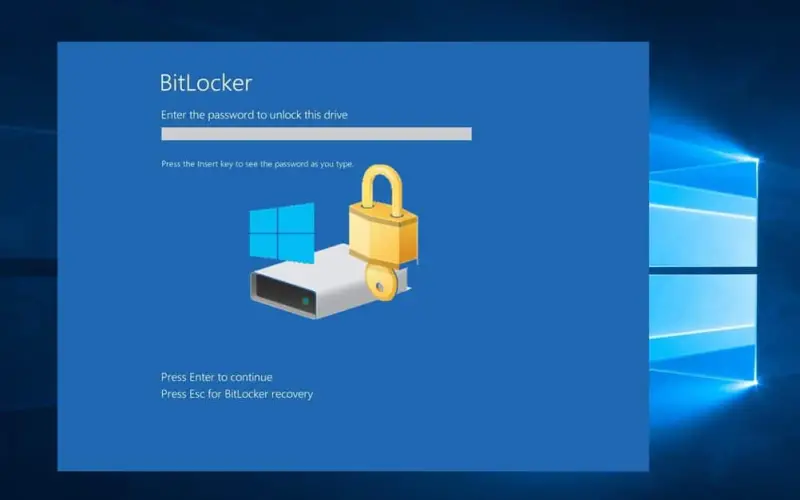
Microsoft’s tightly integrated BitLocker solution offers full-disk encryption capabilities protecting data at rest on Windows devices utilizing Trusted Platform Modules that store encryption keys separated from protected assets. Enables transparent file encryption across desktops, laptops, and tablets without hindering workforce productivity or requiring special training. Keys integrate with domain ActiveDirectory providing centralized administration control over encryption policies like automatic device lock when disconnected from corporate networks or after multiple failed login attempts. Implementation requires professional IT consulting guiding architectural decisions, and integrating key management infrastructure with backup systems and recovery processes. BitLocker provides a credible defense-in-depth data protection foundation; yet lacks the convenience and flexibility of third-party alternatives equipment with expansive cross-platform support.
3. Folder Lock
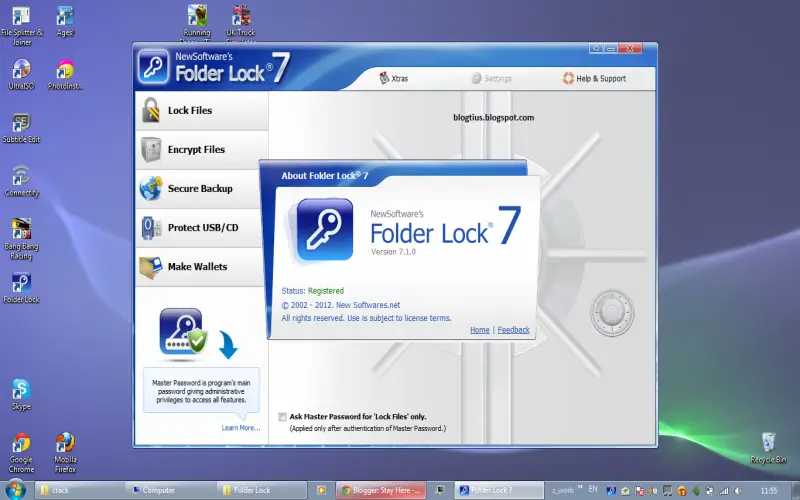
Multipurpose data protection suite securing files within digital vaults encrypted using AES 256-bit encryption alongside the option for archives protected utilizing up to 448-bit Blowfish encryption. Straightforward workflow facilitates easy file uploads encrypted automatically before transmission over HTTPS utilizing SSL/TLS certificates. Empowers creating encrypted wallets securing downloaded web content, auto-encrypted virtual drives, and self-decrypting exe files for sharing securely via email. Key differentiator includes encrypted online file backup capabilities, allowing versioned cloud storage integration with Dropbox and Google Drive. Centrally administered through a web-based console enabling remote user provisioning, and access policy configuration like timefencing. Advanced features include anti-keylogger defenses, password recovery tools, and remote file shredding.
4. LastPass
Leading freemium password manager providing robust encryption capabilities securing credentials, sensitive information entered into web forms, and digital notes across vast device ecosystem encompassing mobiles, desktops, and browsers. Default AES-256 bit encryption with the option to enable multifactor authentication using YubiKey hardware keys bolstering defenses. Browse anonymously using masked emails and auto-generated filler credentials protecting identities. Standout features include password inheritance enabling secure sharing credentials between permitted users and emergency access to designate trusted contacts provided encrypted vault access if unexpected situations arise.
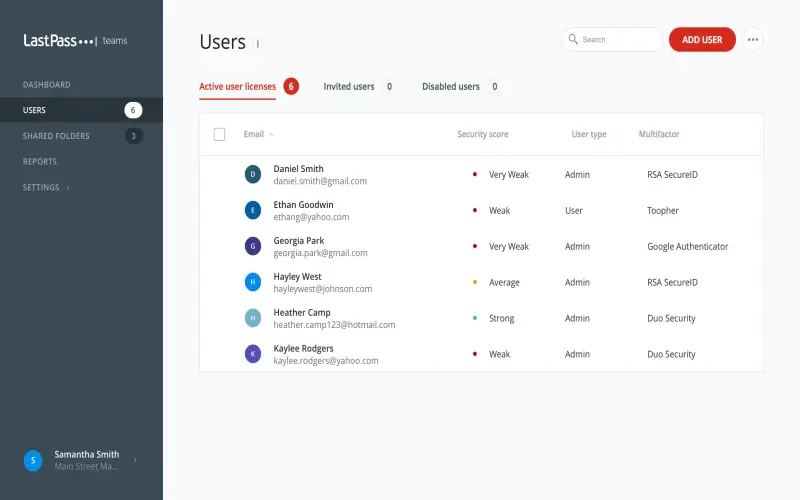
5. AxCrypt
Longstanding freemium Windows encryption stalwart touting AES 128-bit encryption providing basic yet adequate protection for ad-hoc everyday file encryption/sharing needs. A simple workflow allows right-clicking files for encrypting via personal keys with added password protections plus an option enabling one-time decryption links facilitating secure transmission of encrypted documents. Key limitations include a lack of centralized controls, expanded platform support, chatty notifications, and uninstallations that can leave keys lingering adding potential vulnerabilities. Yet provides sufficient lightweight encryption great for encrypting a few files fast without learning complex software.
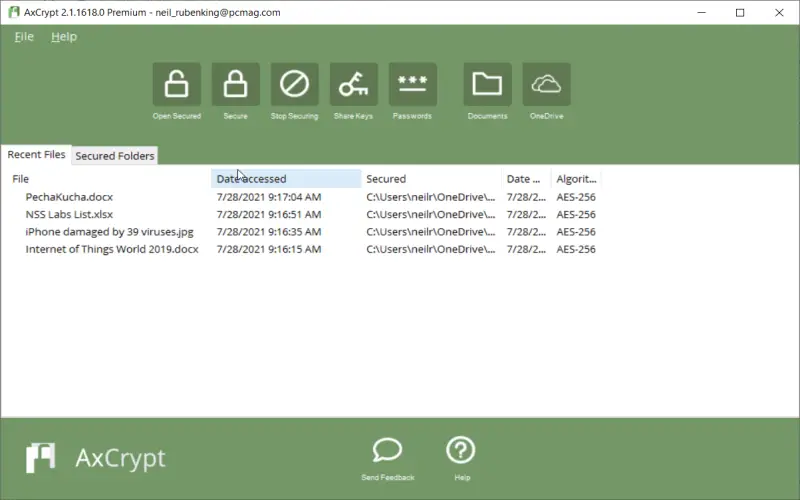
6. CryptoForge
Versatile freemium encryption tool empowering creating encrypted vaults securing unlimited data volumes comprising files, documents, and images across Windows, MacOS, Linux, and Android platforms. Employs military-grade AES 256-bit encryption alongside salted SHA-512 password hashing. Core file-focused capabilities augmented through encrypted chat and cloud storage integration. Intuitive browser-based and mobile apps enable easy sharing of encrypted files. Options for securely wiping vaults when compromised. Centralized server solutions are available for managed deployments. Licensing higher-volume business usage requires switching to paid plans. CryptoForge delivers cross-platform encrypted vaults alongside messaging and cloud storage bolstering data-protection postures.
7. Avast
The core capability of business-oriented Avast SecureLine VPN provides always-on encryption solutions securing files directly within Windows Explorer and MacOS Finder using virtual encrypted drive technology supporting AES 256-bit encryption alongside standards like XTS, CBC encryption modes plus old-school SHA-256 hashing. Straightforward operation facilitates seamlessly moving files into protected digital vaults auto-encrypting data, providing resilient protections if devices get compromised by malware or lost leaving sensitive information vulnerable. Capabilities encompass securely sharing password-protected links to encrypted files. Avast’s antivirus integration adds advanced ransomware detection, and data shredding tools while their VPN service enables securely accessing corporate data from mobile devices using enterprise authentication options including SAML and MSI packages.
8. SensiGuard
Taking a distinct approach, SensiGuard specializes in encrypting Outlook emails and attachments before transit. Users seamlessly exchange encrypted messages without requiring recipients to run any additional software. The tool caters to compliant communications across sectors like healthcare, finance, and law. However, securing Outlook-based data flows means SensiGuard skips directly protecting local files and folders. The niche functionality warrants evaluating organizational use cases.
9. 7-Zip
Extensible open source file archiver touting 256-bit AES encryption integrated natively within the context menu of Windows file explorer allowing easily protecting file/folder contents securely compressed leveraging 7-Zip’s high-compression ratio over stock ZIP. Encrypted archives remain portable across platforms with decryption possible directly within 7-Zip’s MacOS and Linux apps. 7-Zip compares favorably against WinZip and WinRAR in terms of compression ratio and security foundations through AES and authenticity validation via CRC32 checksums. Core capabilities are best suited for manually encrypting a few archives ad-hoc instead of securing numerous dynamic files.
10. VeraCrypt
Advanced disk and file encryption utility based on discontinued TrueCrypt providing enhanced security foundations for power users, and corporations through Western sophisticated encryption. Facilitates full disk encryption across Windows, MacOS, and Linux devices using cascaded algorithms(AES, Serpent, Twofish) run through thousands of iterations alongside 448-bit salted hashing securing passwords/keys. The preboot authentication step adds a layer hindering unauthorized data access if devices are lost/stolen. Enables creating virtual encrypted disks, and opening encrypted partitions.Lacks native remote management capabilities and collapsed TrueCrypt auditability concerns linger despite original issues. VeraCrypt provides corporate-grade open-source transparent disk/file encryption solutions for securing sensitive data cost-effectively.