Today, we live in an era where technology is rapidly advancing with a high level of connectivity. It has changed the way we communicate, work, and conduct our routine activities. The digital platform provides enhanced productivity and connectivity and effective solutions for complex problems. However, it has its own set of vulnerabilities. It could be related to either privacy, security, or ethical considerations. Technological breakthroughs happening every other day raise several concerns regarding data protection, cyber threats, and new challenges posed by AI innovations. Mobiles have become an indispensable part of our life. Today, we have smartphones and tablets that easily fit in our pockets. With a simple touch, we can do anything from chatting with our friends and relatives to conducting business meet-ups and more. Mobile vulnerabilities represent the weakness or security risks in our mobile devices that are detected quickly and exploited by cyber scammers to gain unauthorized access, as well as misuse personal data. A lot of our personal information is stored in our phones, so it is vital to understand and address the mobile vulnerabilities that we can encounter anytime. For your better understanding, we have listed down the Top 10 mobile vulnerabilities.
1. Insecure Data Storage
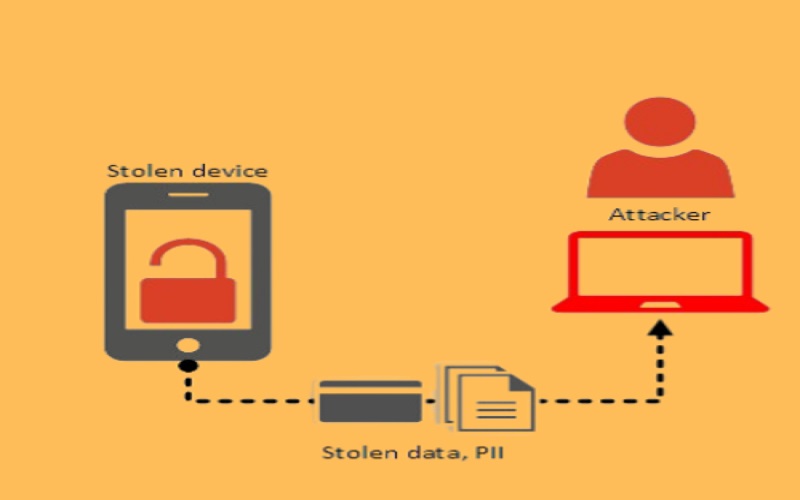
At times, there are chances that your phone gets stolen or misplaced in a public place. In such situations, if it falls into the hands of an attacker, there is a high chance that they may try to access your device’s personal information and sensitive data, which you have stored in your mobile phone. These people exploit vulnerabilities like weak encryption, insecure data storage, and improper handling of user credentials. In order to avoid such situations, it is preferred to encrypt your mobile phone’s data, use an access authorization mechanism, and restrict the app’s access to stored data.
2. Platform Misuse
Every smartphone has its guidelines for the safety purposes of its users. But some applications in our mobile phones makes inappropriate use of these guidelines and violates them. Platform misuse refers to the misuse of any platform feature of the Android or iOS system, such as misuse of the iOS Touch ID, incorrect use of the iOS keychain, and Android intents that permit unauthorized execution. It is best to restrict app communication and connectivity to prevent platform misuse and use limited protection for iOS keychains.

3. Authentication Issues
Sometimes, our mobile phones fail to recognize users identity. In such cases, fraudsters and scammers can access the device using default credentials easily. They often bypass authentication protocols due to poor implementation and direct communication with the server. In such situations, it is better to verify and maintain the user ID where the transmission of confidential data is involved. Do not store passwords locally, and try not to use four-digit passwords.

4. Insufficient Cryptography
Our system’s cryptography gets hampered if the algorithm used for encryption and decryption is weak or if there is an error in the process. If cryptography is not implemented correctly, it is easy for attackers to convert sensitive information to its original form and access it unethically. It is advisable to avoid storing large amounts of data in mobile phones and use robust cryptography algorithms to minimize risks.

5. Unsafe Communications
If the data is not securely encrypted, anyone monitoring your system network can intercept and decrypt the encrypted information sent over the wire. These data transmissions can be interrupted by proxies, cellular towers, or scammers through compromised networks. To ensure secure communication, use a signed and trusted CA certificate, use SSL/TLS certifications for transmissions, and try to send data to the back-end API.

6. Insecure Authorization
If the authorization policies are not transparent and secured, it would be difficult to differentiate between a regular user and an admin user who has the authority and permission to access data. If identity is not adequately enforced and the user is not authorized, it will be easier for hackers to log in and conduct illegal transactions on your device. Insecure direct object reference enables attackers to access important files and data. To obtain authorization, avoid granting access and use back-end codes for authentication.

7. Code Tampering
Often mobile play stores contain tampered or manipulated versions of the original app in which the spammer changes the app’s binary and adds malicious content to it. They re-sign the tampered apps and publish them on third-party app stores. Through phishing, they trick the victim into downloading such apps on their phones. To prevent code tampering, use code signing certificates to identify code changes. Implement anti-tampering techniques such as checksums, code hardening, and other validation methods.
8. Reverse Engineering
Attackers can reverse engineer the app and decompile it for code analysis. This approach helps threat agents understand and modify the code for harmful purposes, such as transmitting unwanted advertisements. After the app’s performance is determined, they adjust it using binary inspection tools. To prevent reverse engineering, use debugging tools, develop codes using C and C++ ,and use binary packaging to avoid the decompilation of codes.

9. Low-Quality Client Code
If the quality of the code deteriorates, it may lead to performance degradation and increased memory consumption. Many people prefer third parties to build their applications. Using different coding techniques depreciates the quality of the client’s code. To mitigate this issue, write code that is easy to understand and well-documented, check for excessive buffering and memory leaks.

10. Additional Functions
Sometimes, additional functions are included in the mobile apps that users cannot see immediately through the interface. Such flaws are then misused by hackers to create security risks. They track file configuration and identify and exploit functionalities to access the back-end system. To resolve such situations, check for the app’s configuration settings to identify hidden switches, check log statements and API endpoints, and confirm that the log does not have content that exposes the privileged accounts.