Privileged Access Management(PAM) as a solution offers security and protects an organization from cybercrimes by rigorously monitoring and preventing unauthorized access to business-critical resources. Using a smart combination of human, processes, and technology gives an idea of who all are using the privileged accounts and their login activities. Privileged accounts like domain admin accounts requires a high level of permission to ensure administrative-level access to critical business systems and operations. Utilizing the best PAM solutions helps an organization reduce the number of employees accessing the company’s sensitive data and services. Also, it adds an extra security level to ensure better compliance with the data regulations. Privileged accounts can easily be altered and misused by cyber hackers. However, PAM solutions assures secured privileged access to high-tier systems. With “just-in-time” access, users get permissions to stay as long it takes to complete their work. Let us explore the Top 10 PAM solutions that offer features like multi-factor authentication, real-time notification, and reporting.
1. Heimdal
Heimdal specializes in PAM solutions that ensures protection against cybercrimes in mailing, websites, and applications. It simplifies the access to privileged accounts and helps in addressing potential security threats. With its user-friendly dashboard, admins can assign permissions, cancel local admin rights, and set escalation periods and log sessions. The generated data can be used for forensic incident analysis to ensure compliance with established standards. Their PAM solutions are cloud-based, which provides a high level of scalability and flexibility for the admins.
2. BeyondTrust
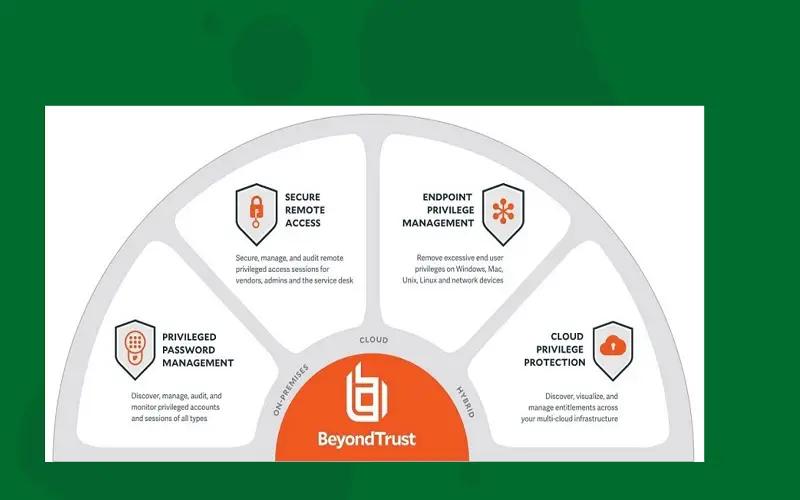
BeyondTrust is the leading vendor of PAM solutions. It offers a high level of visibility across the endpoints, cloud, DevOps, and servers. Without a VPN, it grants privileged remote access for internal auditing and management. The privileged remote access integrates with BeyondTrust’s Password Safe to store the password in the vault and prevent potential credential exposure during the session log. Admins can also set up notification alerts to stay informed when the user accesses the Privileged Remote Access.
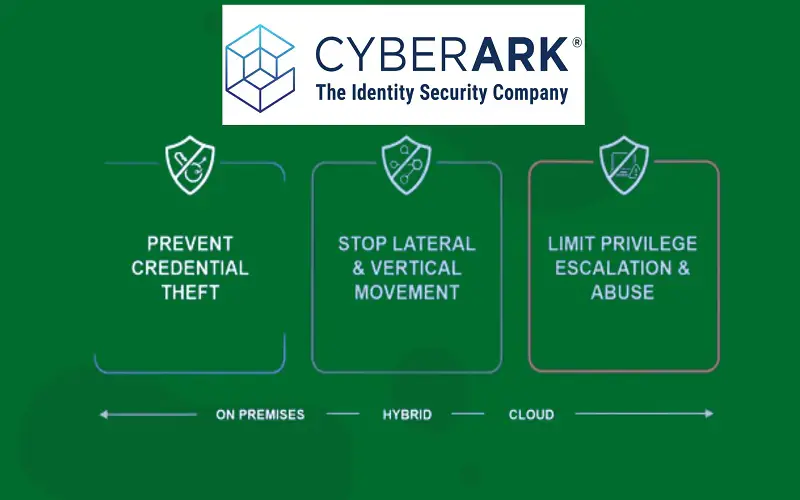
3. Cyberark
Cyberark holds the largest share of the PAM market. It provides enterprise-level solutions to enable IT teams to secure and manage privileged accounts. It offers more than 500 “out of the box” integrations. It gives a transparent view of those who try to access the critical system without the permission. Storing the credentials in the vault prevents unnecessary credential exposure by the user. Cyberark’s PAM solution enables the IT team to record privileged sessions with an encrypted password. These recordings allow admins to view log-in activities and detect any suspicious activities.
4. StrongDM
The PAM solutions offered by StrongDM enable businesses to quickly implement just-in-time access for their cloud and modern databases. Users are assigned temporary permissions according to their roles. Their credential leasing feature allows automatic input of login credentials during user sessions without exposing them to the end user. It also protects against credential thefts by automatically locking the account after multiple failed login attempts.

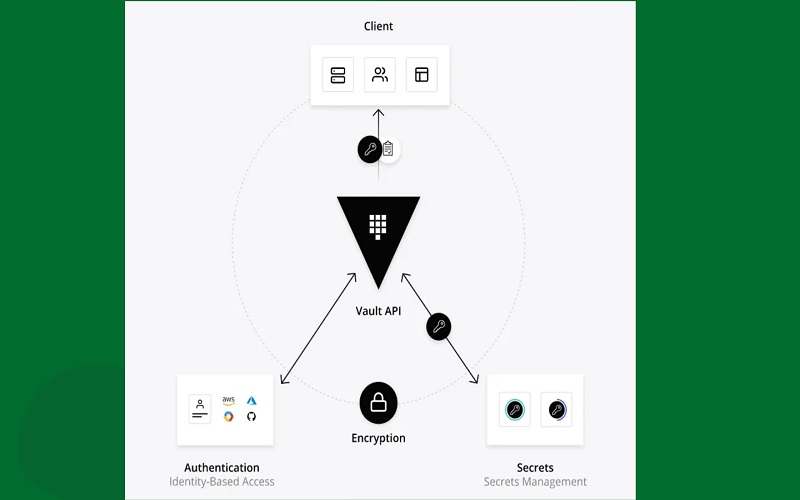
5. HashiCorp Vault
HashiCorp Vault’s security solutions helps in storing and controlling the access to encryption keys, passwords, and certificates. It automates the app delivery and generates more than 10,000 tokens daily. They have three pricing models:
- self-managed option,
- a managed cloud option and
- a self-hosted option
Each credential has a lease, and once the lease expires, the credentials are replaced. HarshiCorp uses Boundary products to offer just-in-time access across the cloud and server.
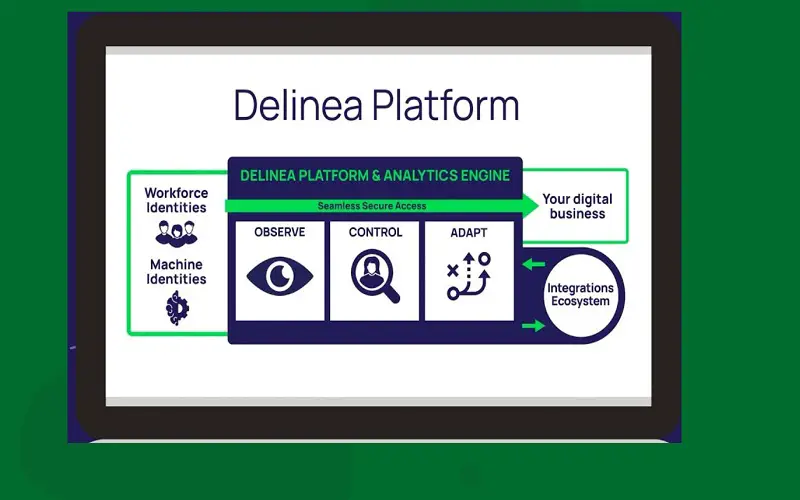
6. Delinea
Delinea (a merger company of Thycotic and Centrify) offers Top PAM solutions for data protection, securing code, endpoint security, and controlled cloud access. Its secret server solution offers an encrypted storage vault for storing unlimited secrets on the cloud and premises. It utilizes a least-privilege policy to maintain its identity with RBAC. Other features of Delinea are robust reporting, automatic password changing, and checking for active passwords.
7. JumpCloud
JumpCloud PAM solutions prevent unnecessary access by the user using multi-factor authentication and a single sign-in feature. This way it eliminates the use of multiple passwords for login. All the workstations and servers are accessible from a single location. It also provides live support to the companies using their services. Other notable features of JumpCloud’s PAM solutions are SSH key management, robust password management, and admin policy settings.

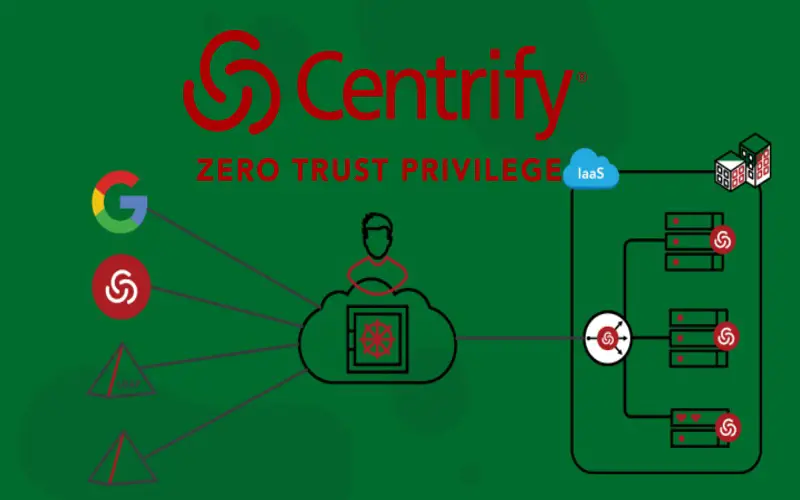
8. Centrify
In Centrify Privileged Access Services, only authorized users can access IP address and password in a secured vault. User’s are authenticated with MFA and there log-in activities are supervised. After the session, credentials are rotated automatically to prevent multiple usage. Available as a SaaS solution, it does not require software installation. It seamlessly integrates with all other software solutions to handle all PAM needs.
9. Broadcom
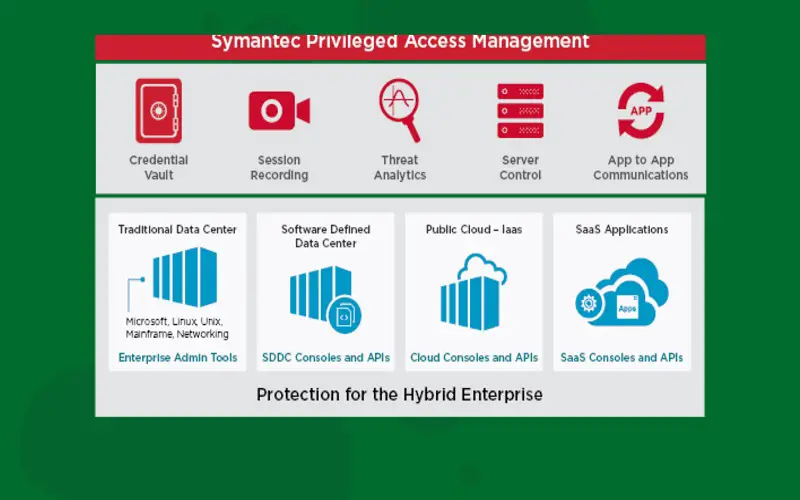
Broadcom’s Symantec Privileged Account Management enables businesses to monitor and control access to the high-tier accounts. Their web security solution helps in ensuring compliance with the established industry standards. It stores admin passwords and SSH keys in a secure vault. With two-factor authentication, users get access to the vault and when the session is over, credentials are rotated to prevent breaches. Symantec’s PAM solution applies ML techniques to compare current actions with old ones and identify suspicious acts.
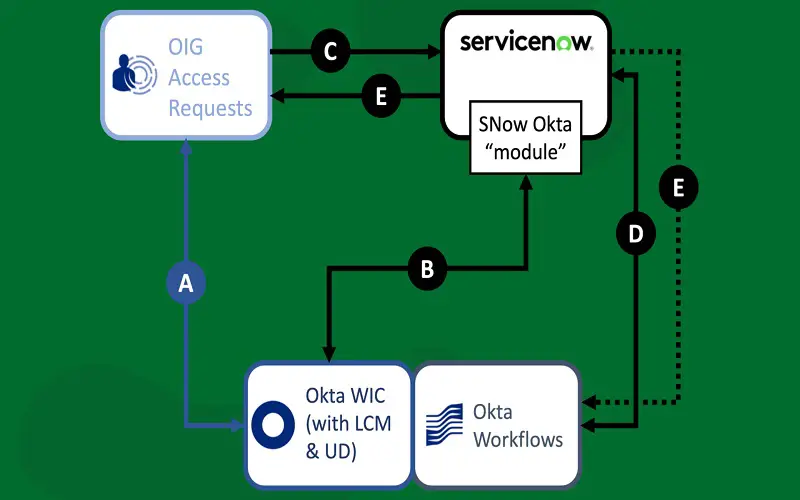
10. Okta
Okta offers a cloud-based access management solution to secure user access to company accounts, applications, and systems across multi-cloud environments. The platform provides services of adaptive MFA, IGA, and lifecycle management. It enables companies to implement least privilege access before granting the elevated access permissions. It can potentially track and store all the local privilege accounts in a security vault. It also allows companies to monitor and capture privilege session activities and audit them to meet compliance requirements.