What is Cloud Security?
Cloud security means processes, controls, and arrangements of technologies that coordinate for protecting your cloud-based infrastructure, information, and frameworks. It’s a sub-area of PC security as well as information security. So, cloud security is a joint obligation between the client and their service provider. To safeguard your privacy, you want to execute a cloud security strategy. This protects your information and you from the legal, monetary, and reputational problems of data loss.
1. Employ a (Cloud Access Security Broker)
Using a CASB is the primary instrument to execute cloud security best practices. This software sits between you and the service provider and maximizes security controls in the cloud. Besides, a CASB gives a high-level cloud security toolset to execute information security approaches and offers visibility of the cloud ecosystem.

2. Encryption is key
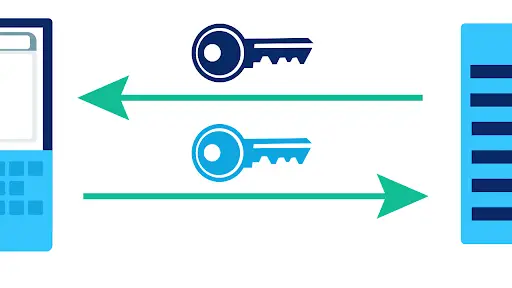
Cloud encryption is necessary for security. Ask your provider how information is managed. To guarantee the assurance of your information before it leaves your business, you can scramble to the organization’s edge, ensuring the development of information in the cloud is protected. When the information is encoded, keep the keys that speed and unravel your data. Having both of these implies that even if the data is used by a third party, all data requests will need to involve the owner.

3. Passwords
“Passwords contain not less than eight characters, one number, mixed letters, and symbols. But, these can be broken by hackers easily. Don’t fall into that risk category. Ensure that unique passwords are unique.

4. Keep up with the Highest Encryption Levels
Your information might become vulnerable to higher risk while conveying it between the cloud administration and your organization. Encryption helps in assisting with keeping up with full command over the information.
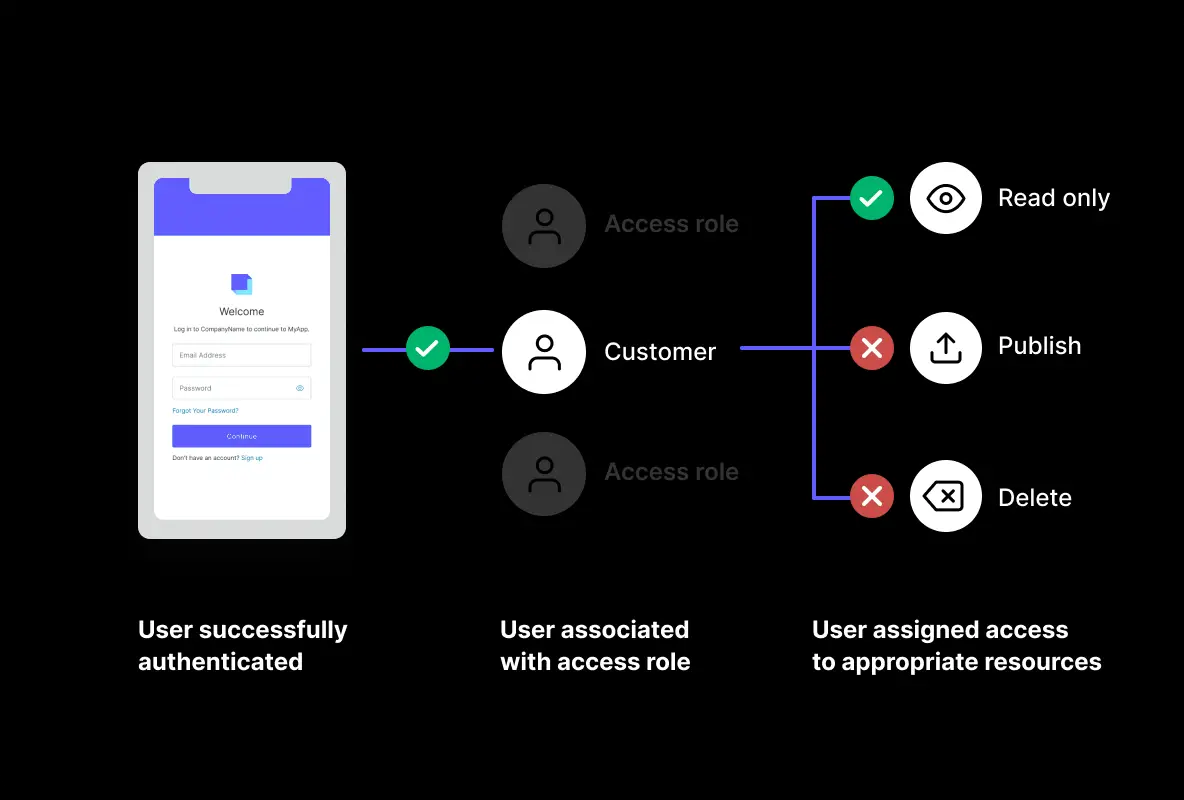
5. Authorize Strict Control of User Access
This cloud security best practice assists you with managing the clients who attempt to get to your cloud services. Start with zero trust, simply giving clients admittance to the information and frameworks they need. To decrease complicity while authorizing approaches, build well-defined groups with explicit roles to consider admittance to chosen assets. Moreover, you can add clients directly to gatherings rather than getting access to every single client.
6. Select a Reliable Cloud Service Provider
You ought to collaborate with a solid cloud service provider. Select a provider who offers in-built cloud security and follows the most significant levels of business best practices. You should try to confirm their security accreditations and compliance.

7. Give Anti-Phishing Training to Employees regularly.
Hackers can access data by taking login information through friendly design procedures, for example, phishing, ridiculing sites, and spying.

8. Consider Cloud-to-Cloud Backup Solutions
The chances of you losing information due to your cloud supplier is extremely low – however, losing that information because of a human blunder is high. Assuming that a worker ought to incidentally erase data, a hacker obtains a password and corrupts the data; there isn’t anything Microsoft can do beyond a specific period.

9. Arrange Data
Information breaks and information loss are some of the top cloud security dangers. Security of cloud information ought to be the target of business associations worldwide. It is necessary to identify which information in your company requires the most significant security. Sensitive data requires the most robust protection, so arranging data relies on its importance.

10. Cloud security requires the right tools.
Specialists, by and large, worry that security shouldn’t keep organizations from utilizing cloud services. Organizations have fewer security issues with cloud-based workloads than with those that run in conventional server centers.
One thing is evident from our rundown of best practices it’s that solid cloud security depends on having the correct apparatuses set up. By following cloud security best practices and executing suitable security tools, organizations can limit dangers and make the most of the advantages cloud computing offers.


















