Quantum cryptography leverages principles of quantum mechanics to enable secure communication between two or more parties. As computing power grows exponentially, traditional encryption schemes face potential vulnerability from attacks by quantum computers. Quantum key distribution provides an information-theoretic secure solution, guaranteed by laws of physics. Over recent decades, intense research has advanced practical quantum cryptography from theory to experimental demonstrations now nearing real-world deployment. This article outlines the top 10 most promising quantum cryptography protocols as robust alternatives to guard sensitive data in an age of heightened cyber threats. I outline below the top protocols that stand out for versatile security applications. The list spans foundational quantum key distribution protocols designed for point-to-point quantum links. It also includes extensions that enable more complex communication among multiple parties. As keys become compromised far too easily these days, quantum cryptography finally offers foolproof security foundations.
1. Quantum Key Distribution Using W State
Quantum key distribution represents the most mature application of quantum cryptography. The W state protocol extends capabilities from single sender and receiver to multi-party scenarios. Researchers demonstrated W state distribution among three parties under laboratory conditions back in 2003. As opposed to quantum channels between each pairing of participants, W state sharing enables secure communication between any two with authentication from the third. The intricate quantum entanglement scheme warrants no eavesdropper can access distributed keys.
2. Quantum Private Queries: Security Analysis
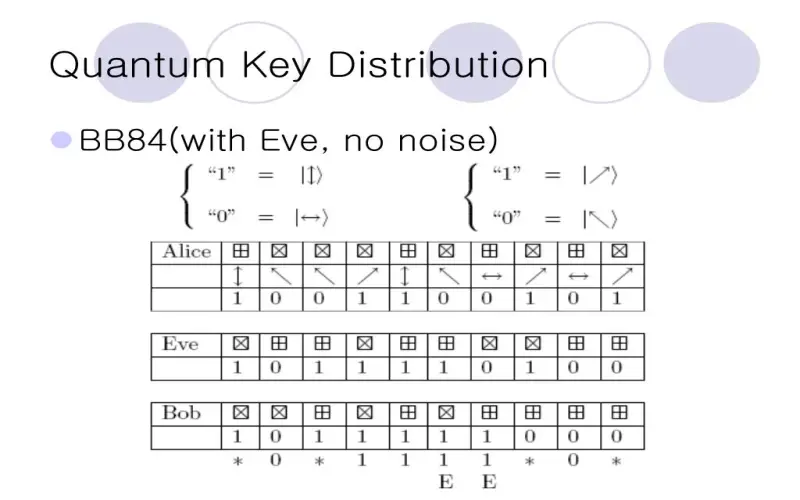
Private database queries, such as search engines, should not reveal contents to the server. Quantum private queries based on oblivious transfer solve this dilemma. The server sends an encoded database to the client. The client can decode their desired item without the server knowing which item they retrieved. A 2021 analysis proved information-theoretic security for the protocol against the most general attacks. As users grow wary of data privacy violations, fast private queries warrant applications for confidential searches or classified databases.
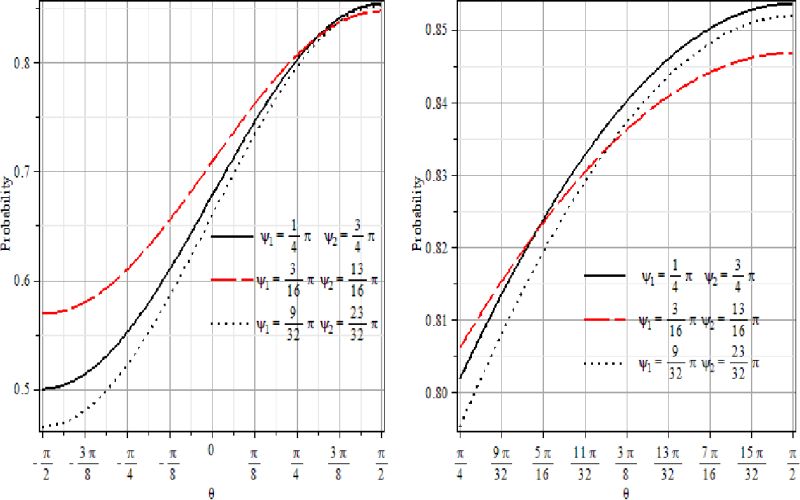
3. Multi-User Quantum Private Query
Most private query protocols focus on two-party communication. Researchers recently expanded quantum private queries to the multi-user domain. The new scheme enables a server to share a database securely among many authorized clients. By transmitting encoded quantum states to each client, the database items remain oblivious to all parties without appropriate decoding. The protocol relies on delicate quantum state engineering techniques. As part of regular reporting, the team quantified higher information leakage margins compared to an ideal scheme. Nonetheless, the expanded capabilities open new avenues to privately share sensitive data at scale.
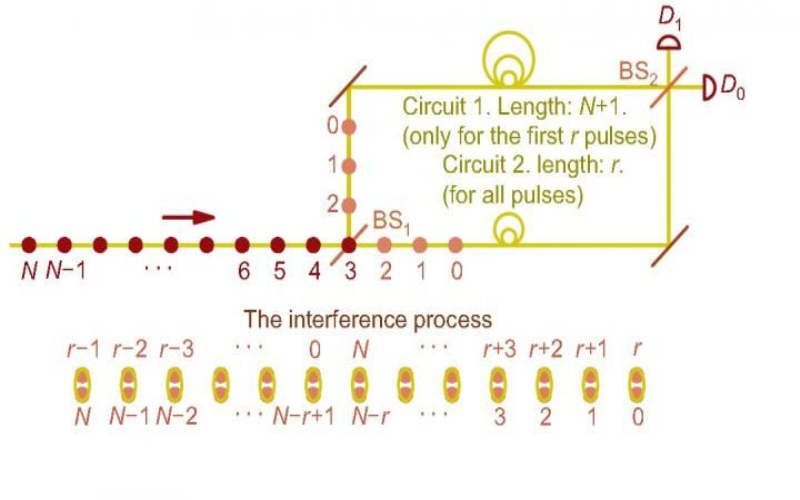
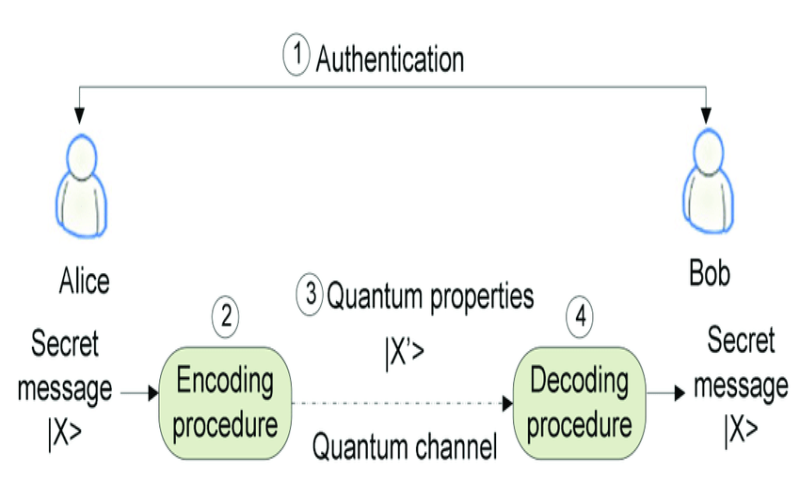
4. Quantum Secure Direct Communication: Principles, Current Status
Beyond distributing secret keys, quantum physics also enables secure direct communication. The sender directly transmits private messages over a quantum channel to the receiver without encryption. Intrusion results in detectable disturbance to the quantum states. Initial concepts date back decades. But years of optimization now achieve high capacities with simple hardware arrangements. Recent refinements in Australia provide security proofs across a range of adversary models from passive to active attacks.
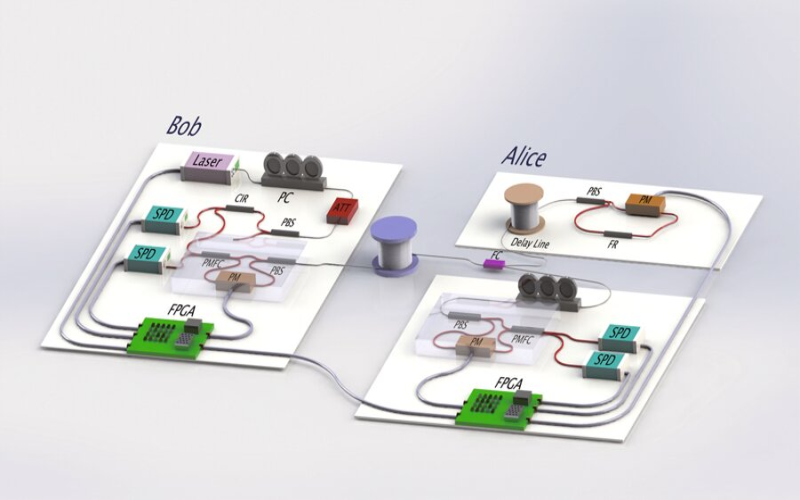
5. Multi-Party Quantum Key Agreement
Classical cryptography often relies on a trusted central party to coordinate key exchanges between multiple users. Quantum solutions now allow key agreement directly between all involved parties without this vulnerability. The multi-party protocols utilize quantum state transmission and measurement techniques to guarantee security. Cryptanalysis verifies robustness against both external eavesdroppers and internal betrayers. Though complex in early iterations, researchers recently reduced the sophisticated techniques down to preparations and measurements. The multi-party quantum key agreement now becomes viable with existing technology. As distributed networks prevail across industries, such versatile cryptography will help secure the orchestration of collective communications against both external and internal threats.
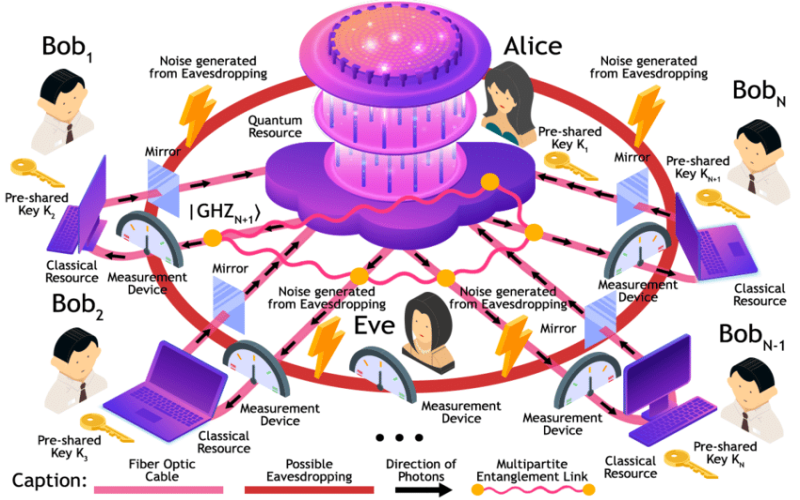
6. Measurement-Device-Independent Multi-Party Quantum Key Agreement
Measurement-device independence closes security loopholes from imperfect detectors that left quantum protocols vulnerable. By using untrusted measurement devices, new protocols remove assumptions about precise detector efficiencies. The detectors no longer require calibration or monitoring. Researchers recently expanded this methodology to the domain of multi-party quantum key agreement. The team reduced the necessary quantum resources compared to other protocols with equivalent security. Compatible with decoy-state preparation, the technique becomes implementable with current technology. As DBAs need to consider ongoing calibration of quantum hardware prohibitively resource intensive, a measurement-device-independent approach proves promising.
7. Quantum Secure Direct Communication (QSDC) – International Defence Conference
An international defense conference session highlighted quantum secure direct communication as the future of classified communication. Compared to quantum key distribution, QSDC offers advantages for specialized applications. It ensures real-time secure transmission without pre-establishing keys, smoothing operations for agile defense teams. Cryptographically secured against brute force attacks, QSDC leaks no partial information to eavesdroppers. Integrating QSDC with existing infrastructure, defense agencies can augment legacy communication systems with fundamentally secure quantum links. Already demonstrated over 200km, separate teams now collaborate to test QSDC across global distances. Panelists contend wide adoption remains realistic within the decade. While risks from quantum computing loom, quantum communication itself offers an unbreakable sword against adversaries.
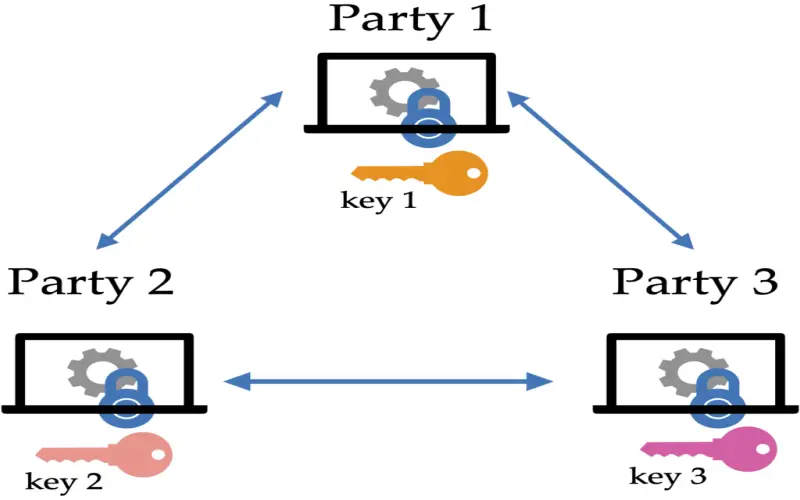
8. Secure Multi-Party Quantum Key Agreement
Quantum solutions now move beyond pair-wise communication to enable secure keys between multiple users. A North American team recently developed a multi-party protocol with security proofs even given unreliable quantum memory. Each participant performs quantum state preparations, transformations, and measurements. Then classical post-processing derives a final shared key. All operations utilize the technology available today. The modular design allows for the optimization of each component for efficiency. Testing over spoofily manufactured quantum channels confirms robustness. With versatility for network configurations without a central authority, the secure multi-party protocol promises applications from banking to national security domains.
9. Experimental Quantum Aecure Direct Communication With Single Photons
Photons represent leading qubit implementations for quantum transmission across networks. This experimental QSDC protocol uses a single photon source to demonstrate principles of quantum secure direct communication over optical channels. By encoding message bits through photon polarization or occupancy number states in two optical modes, key extraction becomes accessible only to legitimate receivers. Field tests across 100 km of commercial fiber with polarization coding achieve 85%-89% transmission accuracy, demonstrating viability for metropolitan distances. While photon loss remains a key challenge, single photon QSDC moves direct quantum communication closer to widespread adoption.
10. Continuous Variable Quantum Cryptography
Continuous variable quantum cryptography (CV-QKD) protocols carry information in continuous degrees of freedom of the electromagnetic field, unlike discrete variables. Continuous variable quantum key distribution (CV-QKD) represents a practical solution for metropolitan-scale quantum networks with wavelength division multiplexing. Multiplexing compatibility significantly bolsters adoption for telecom infrastructure leveraging existing fiber assets. CV-QKD uniquely suits coherent detection, enabling resilience against background noise that hinders performance.