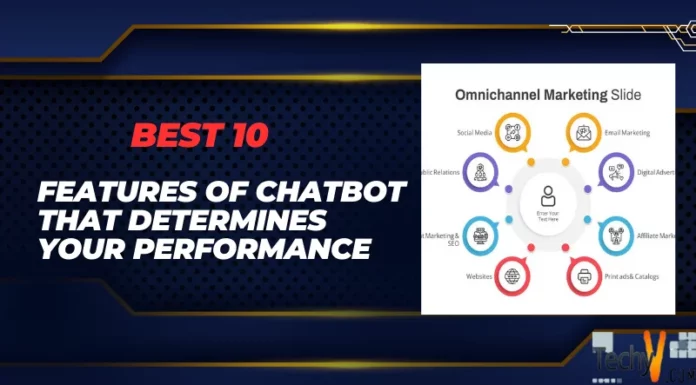
To protect and transmit data in a way that cannot be intercepted, quantum cryptography employs the inherent features of quantum physics. Data is encrypted and protected using cryptography so that only those with the proper secret key may decrypt it. In contrast to conventional cryptographic systems, quantum cryptography uses physics rather than mathematics as the primary component of its security concept.
1. Quantum Key Distribution (QKD)
A secure form of communication for sharing encryption keys that are only known to shared parties is quantum key distribution (QKD). It exchanges cryptographic keys in a verifiable manner that ensures security using principles from quantum physics.
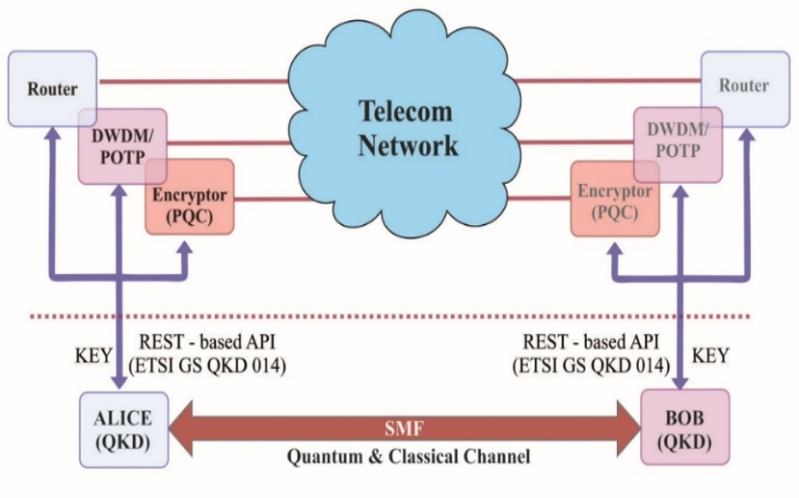
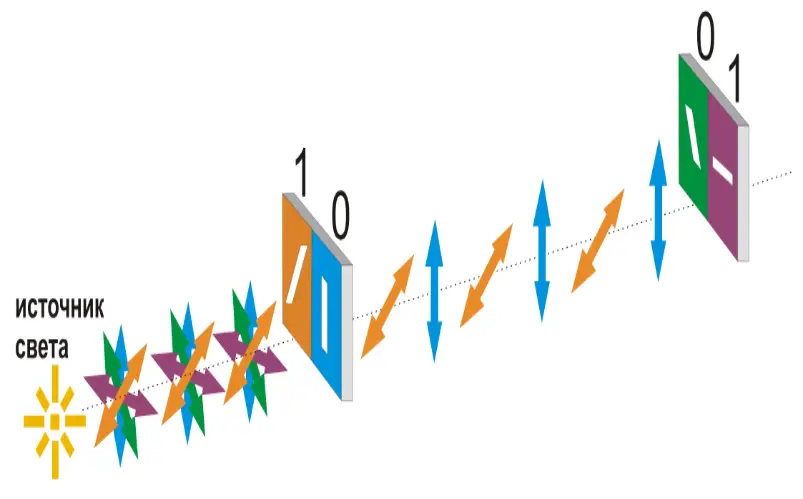
2. BB84 Protocol
In the BB84 protocol, Alice can transmit a random secret key to Bob by sending a string of photons with the private key encoded in their polarization. The no-cloning theorem guarantees that Eve cannot measure these photons and transmit them to Bob without disturbing the photon’s state in a detectable way.
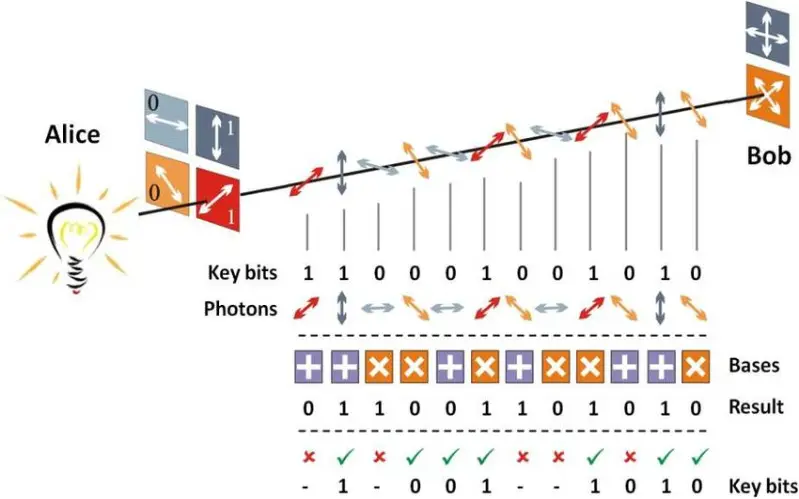
3. E91 Protocol
The important principle on which QKD is based is the principle of quantum entanglement. Two particles can become entangled such that when a particular property is measured in one particle, the opposite state will be observed on the entangled particle instantaneously. This is true regardless of the distance between the entangled particles. It is impossible, however, to predict before measurement what state will be observed thus, it is not possible to communicate via entangled particles without discussing the observations over a classical channel.
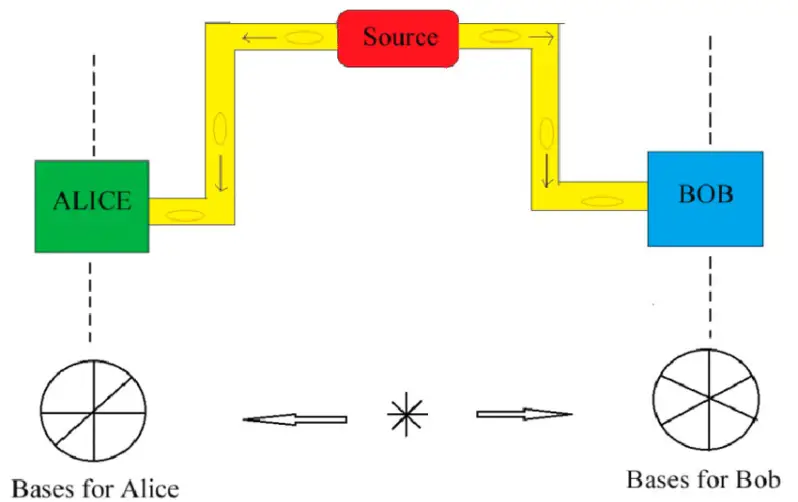
4. B92 Protocol
B92 protocol is a modified version of the BB84 protocol, with the key difference between the two is that while the BB84 protocol uses four different polarization states of the photon, the B92 protocol uses two (one from the rectilinear basis, conventionally H-polarization state and one from the diagonal basis, conventionally +45°-polarization state).
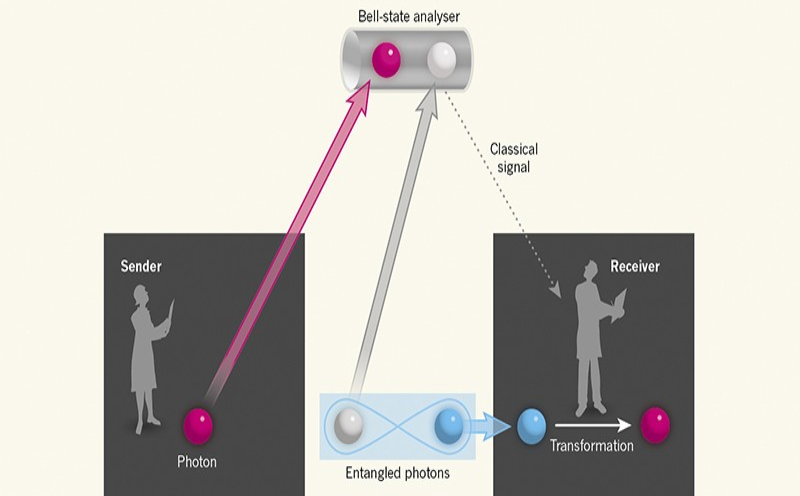
5. Quantum Teleportation
A method for sending quantum information from a transmitter at one point to a recipient far away is called quantum teleportation. While teleportation is frequently depicted in science fiction as a way to move physical items, quantum teleportation only moves quantum information. The specific quantum state being conveyed need not be known to the sender. Additionally, the recipient’s location may remain a mystery, yet classical information must still be transferred from the sender to the receiver for quantum teleportation to succeed.
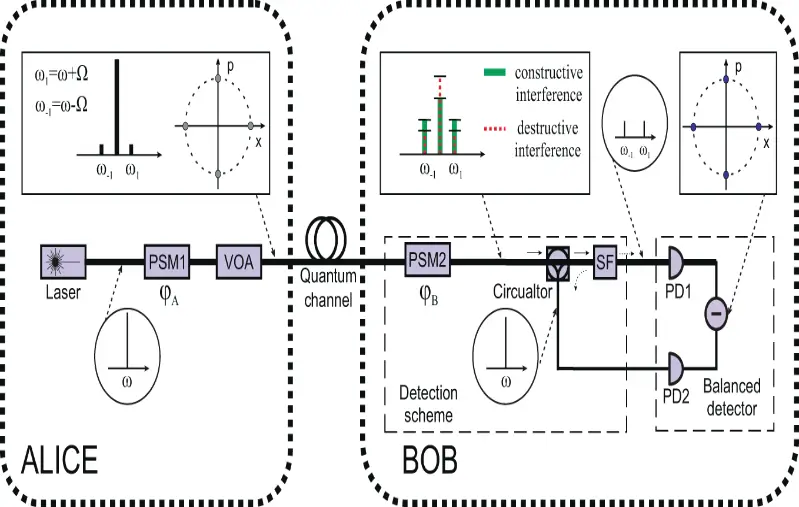
6. Continuous Variable Quantum Key Distribution (CV-QKD)
Continuous-variable quantum key distribution (CV-QKD) is a technology that can potentially provide information-theoretic security to cryptographic systems. CV-QKD is highly attractive thanks to high secret key rate generation over metropolitan distances and integration with the current classical communication networks.
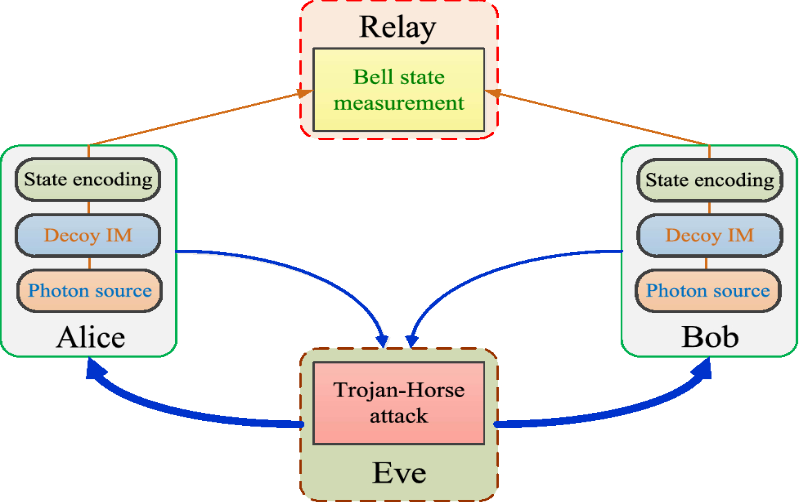
7. Measurement-Device-Independent Quantum Key Distribution (MDI-QKD)
All detection side channels in quantum communication systems can be eliminated by measurement-device independent quantum key distribution (MDI-QKD). But certain presumptions about the sources must be true for the security proofs to work.
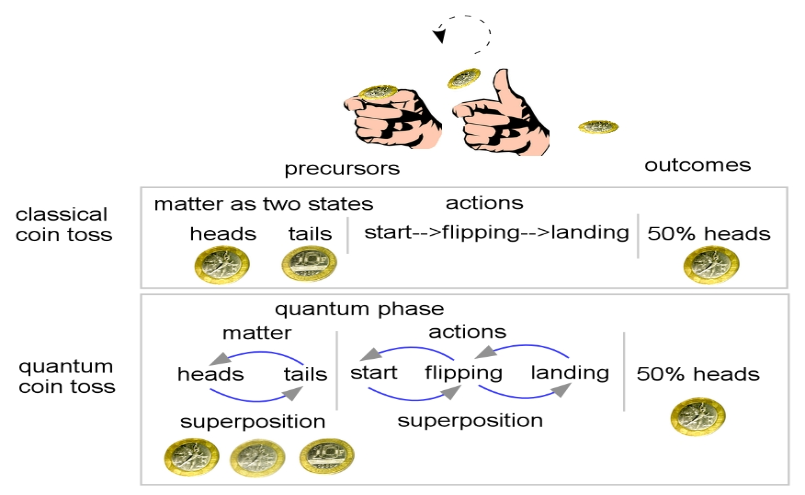
8. Quantum Coin Flipping
Quantum coin flipping is the process of generating random qubits between two participants that do not trust one another since they both want to win the coin toss, which might induce them to cheat in several different ways. The fundamental action of flipping a coin takes place when two players communicate a series of instructions that ultimately produce an output.
9. Quantum Oblivious Transfer (QOT)
The area of cryptography known as quantum cryptography studies the quantum characteristics of materials. Its goal is to create cryptographic primitives that go beyond the capabilities of traditional methods or to enhance those methods already in use. Even though much of the research in this area focuses on quantum key distribution (QKD), significant progress has been achieved in the understanding and advancement of quantum oblivious transfer (QOT). Comparisons between the application structures of QKD and QOT primitives are feasible. QOT protocols enable quantum-safe computation, much as QKD protocols provide quantum-safe communication.
10. Quantum Signature Schemes
A quantum mechanical analog of either a traditional digital signature or, more broadly, a handwritten signature on paper is referred to as a quantum digital signature (QDS). A digital signature, like a handwritten one, is used to safeguard a document, such as a digital contract, from fabrication by a third party or by one of the parties involved.