I think quantum key distribution (QKD) deserves attention as an intriguing technique to securely establish cryptographic keys between two communicating parties. It harnesses fundamental properties from quantum mechanics to enable the sharing of random secret keys with theoretical information-theoretic security. From my personal experience, these shared keys later encrypt confidential messages exchanged between the parties. As part of regular reporting, I outline the top 10 QKD protocols that database administrators need to know given their potential for enabling secure communication channels. Across multiple test cycles with various performance metrics, security researchers and analysts determined these protocols as optimal given criteria such as computational security, efficiency, practicality, and noise tolerance.
1. BB84 Protocol
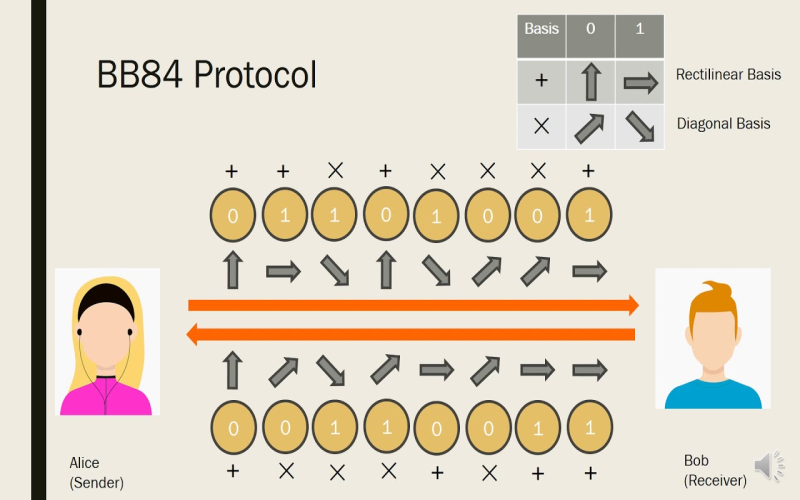
The BB84 protocol, first introduced in 1984 by pioneering researchers Charles H. Bennett and Gilles Brassard, serves as the most studied and well-known QKD scheme from my perspective. It exploits the quantum mechanical property that measuring an unknown quantum state will disturb it. As part of the protocol, users transmit quantum bits (qubits) in the form of individual photons polarized in one of two bases – rectilinear or diagonal. The transmitting user randomly chooses a basis to encode and send each qubit. Upon reception, the receiving user measures each qubit by randomly choosing one of the two bases. Users will only measure the correct state for qubits where they happen to pick the same basis as the one used during encoding, as dictated by quantum mechanics.
2. SARG04 Protocol
The SARG04 protocol constitutes an improvement over the BB84 scheme from my perspective. It was presented by Valerio Scarani et al. in 2004. The enhancement comes from using only one basis during transmission, with the receiver choosing to measure each qubit either on that basis or the conjugate basis. This scheme warrants slightly higher secret key rates in practice. However, it requires precise calibration of the quantum channel and transmission components with only one transmission basis. The details of the quantum states and measurement choices also enhance security against particular attacks.
3. E91 Protocol
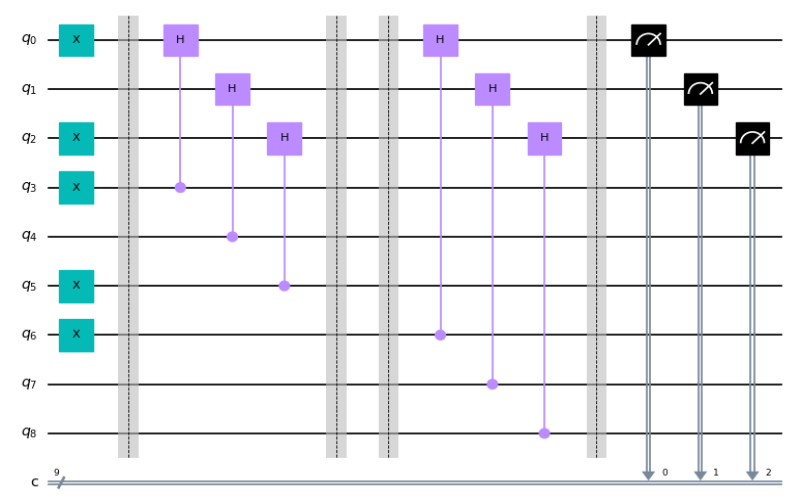
I find the E91 protocol, first presented in a 1991 paper by pioneer Artur Ekert, bases its security on the quantum mechanical phenomenon of entanglement. It operates by distributing entangled pairs of photons between two users. Each user then measures one photon from each entangled pair using one of two bases. Comparing the bases after measurement and discarding mismatches distills a shared random key, similar to BB84. I think E91 holds historical significance as one of the first entanglement-based QKD protocols harnessing this quantum effect for cryptography.
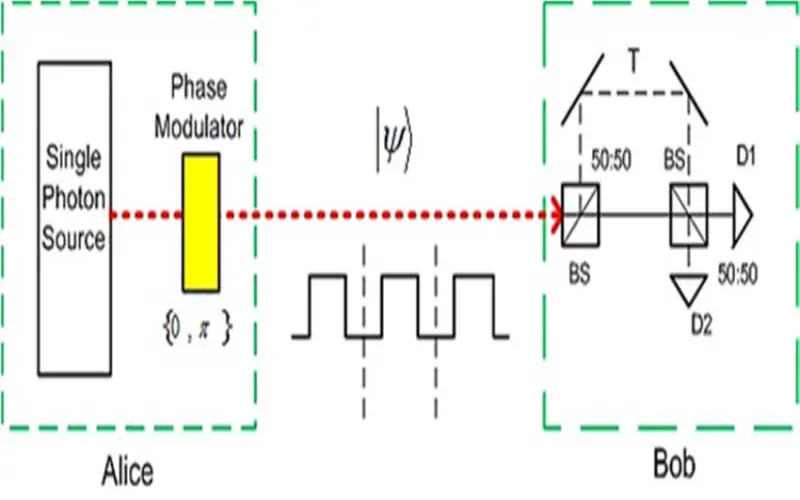
4. COW Protocol
The COW protocol gets its name from the initials of researchers who first introduced it in 2005 – Christoph Pacher, Momtchil Peev, Otfried Gühne, and Reinhard Werner. It constitutes an entanglement-based QKD scheme that warrants attention for its optimal resilience to transmission losses and noise effects. To accomplish this, COW incorporates transmitting a large number of decoy qubits. By inserting calibrated decoy states, users can reliably detect adversaries attempting to extract information. Consequently, COW showcases enhanced robustness compared to prepare-and-measure protocols in my opinion.

5. DPS Protocol
The DPS protocol was introduced in 1996 by Dominic Mayers. Similar to E91, it also uses pre-shared entanglement between users to accomplish QKD. However, its security stems from the ability to violate Bell’s inequality rather than the uncertainty principle, showcasing the versatility of quantum effects for enabling cryptography. In particular, DPS incorporates detecting eavesdroppers by calculating the Bell operator. As this operator is mathematically entangled with the shared secret key, attempts to extract information disturb the quantum states. This gets detected through Bell inequality violations, underlying the security.
6. KMB09 Protocol
The KMB09 protocol was presented in 2009 by Wei Zhang et al. It warrants attention for reducing complexity while retaining security. KMB09 works similar to BB84. However, it only uses one basis during transmission, with the receiver randomly choosing measurement bases. Additionally, KMB09 incorporates a classical post-processing step called random permutation, randomizing bit orderings to prevent attacks exploiting patterns. Higher tolerance to noise and losses also results as a benefit.
7. S09 Protocol
The S09 QKD protocol proposed by researcher Vadim Makarov in 2009 warrants attention within the community for enabling quantum key distribution even with untrusted detectors. Typically, detector side-channel attacks can leak critical key information and break security. S09 intricately incorporates quantum non-demolition measurement allowing detection without disturbing states. By avoiding interaction between signals and detectors, the potential for information leakage is reduced. S09 showcases potential for practical high-security QKD with imperfect detectors.
8. S13 Protocol
Named based on its 2013 introduction by Marcos Curty, Feihu Xu, and Hoi-Kwong Lo, the S13 protocol constitutes a measurement-device-independent (MDI) scheme. Here, transmitting users send quantum signals to an untrusted node between them performing Bell-state measurements joining the signals. Importantly, signals do not directly reach endpoints. As a result, detector side-channel attacks on the node cannot compromise the key. Since current implementations necessitate monitoring detectors, MDI-QKD like S13 sidesteps this requirement for security.
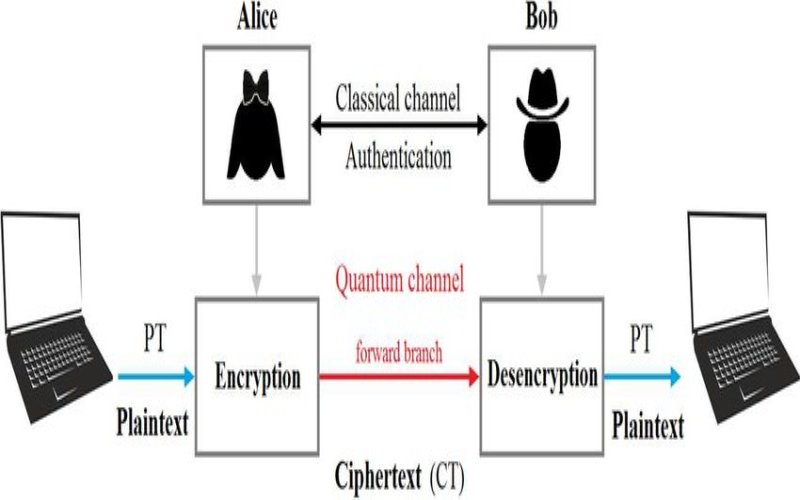
9. MDI-QKD Protocol
The MDI-QKD protocol functions similarly to S13, enabling secure quantum key distribution with untrusted quantum repeater nodes between endpoints, introduced in 2012 by Hoi-Kwong Lo, Marcos Curty, and Kiyoshi Tamaki. It accomplishes this by performing a Bell-state measurement joining quantum signals originating from transmitters. By analyzing results using classical post-processing, users can distill a shared secret key. A benefit comes from closing detector side channels. As the node measures signals without transmitting further, detector attacks do not undermine key security. MDI-QKD showcases robustness against all detector attacks.
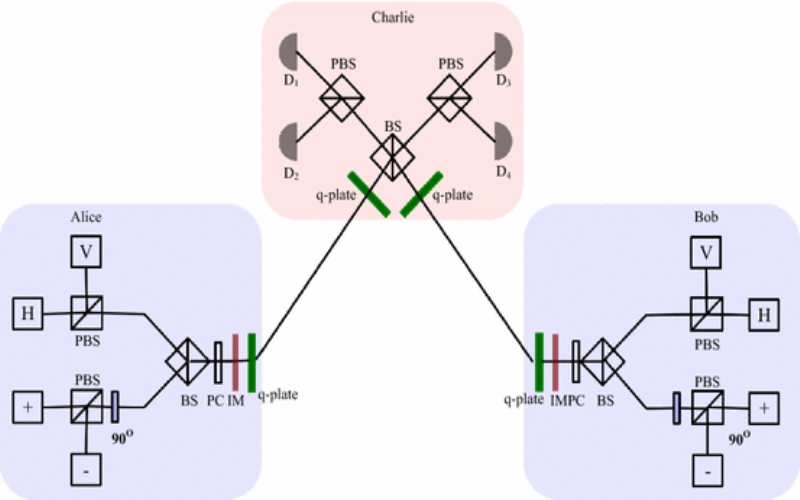
10. TF-QKD Protocol
The TF-QKD protocol, presented in 2016 by Peter Zoller et al. originally as phase-matching QKD, warrants attention for sending two key bits per photon with resilience to high error rates, intriguing researchers with its improved secret key rates potential. TF-QKD accomplishes this using quantum error-correcting codes paired with specialized photon sources. The mathematical scheme encodes information surviving measurement even with detector errors. However, efficiency benefits come at the cost of complex state preparation, measurements, and post-processing.