Ransomware has been one of the biggest emerging threats this year; with ransomware attacks hitting significant organizations such as Puma and accounting for 10% of all data breaches, it is essential to keep an eye on the emerging threat. With newer and newer ransomware families joining the fray, watching for the major players is more important than ever. Today’s article will discuss the Top 10 Ransomware of 2022.
1. LAPSUS$
Lapsus$ is a South American cybercriminal gang that, through their ransomware, hit major tech giants at the beginning of the year. The team used stolen source code to disguise their malware as trustworthy files. In March 2022, they attacked Microsoft, Nvidia, Samsung, and other tech conglomerates such as Globant and T-Mobile. They have been using ransomware as one of the practical tools for their extortions.

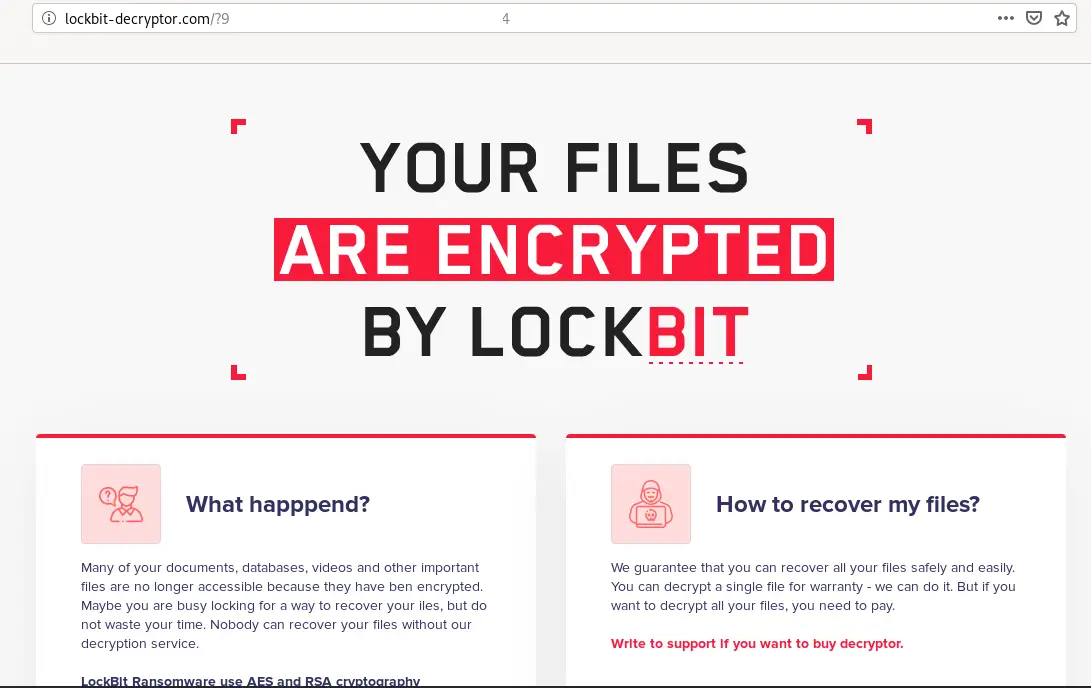
2. LockBit
LockBit, formerly ABCD ransomware, is designed to lock the system user out and block any access attempts in exchange for a ransom. LockBit is smart ransomware as it automatically goes for valuable targets, spreads, and encrypts all the systems on the network. This ransomware has been designed for enterprises and uses tools such as Windows Powershell and Server Message Block to spread.
3. XingLocker
XingLocker is a ransomware that targets the Windows operating system. Being relatively new, this ransomware was built over the popular Mount Locker ransomware and is part of the new ransomware-as-a-service (RaaS) ransomware model. Upon infection, the ransomware will point the user to a tor site where a ransom note will be ready. While not innovative and just a rebrand of another popular ransomware, it is essential to highlight how different cybercrime groups are working on running the SaaS business and how big of a threat ransomware has become.

4. Ryuk
Pronounced as ree-yok and named after a famous anime and manga character in the series Death Note, Ryuk is ransomware developed by the Russian cybercriminal group Wizard Spider’. First appearing in mid-to-late 2018, Ryuk ransomware has been one of the significant threats many organizations are dealing with. Ryuk, unlike other ransomware, specifically aims for high-value targets and encrypts their systems to demand a ransom.

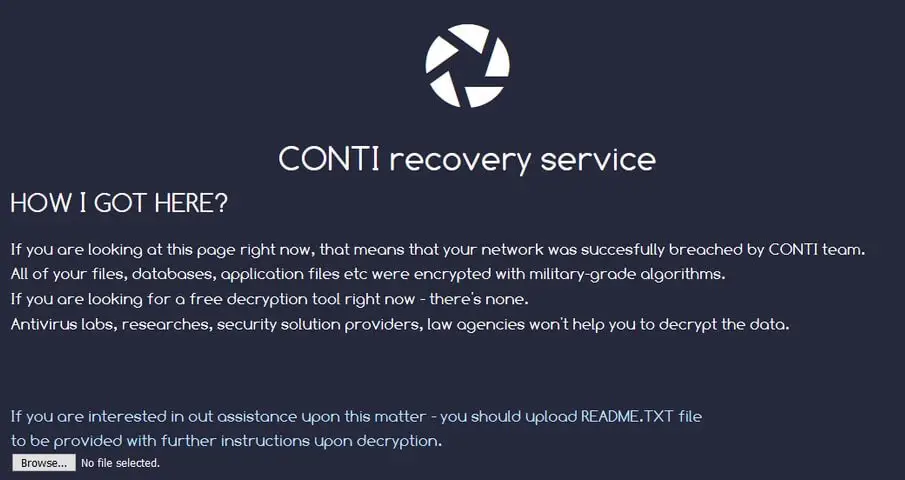
5. Conti
Conti is ransomware recently responsible for a state of Emergency in Costa Rica and has continued to wreak havoc in cyberspace since late 2021. It is also believed to be developed by the Russian cybercriminal group ‘Wizard Spider.’ Conti spreads through phishing, where the attacker sends its victim an email with a link that leads them to a text document. This document, on google drive, leads to the malicious file being downloaded and infecting the system.
6. Magniber Ransomware
Developed and operated by the cybercriminal group Vice Society, Magniber Ransomware is an older malware said to have first emerged in 2017. But weaponized with a new vulnerability named ‘PrintNighmare’ in the Windows Print Spooler service Magniber has reemerged. When Magniber infects a victim’s system, it immediately encrypts all files and leaves a readme.txt file with the demands for payment.
7. REvil
REvil or Ransomware Evil, popularly known as Sodinokibi, is Russian ransomware following the newly emerging Ransomware-as-a-Service (Raas) model. In early January 2022, Russian authorities said they captured the team running the ransomware and dismantled it entirely. However, the malware has been circulating through other groups and is still an imminent threat.
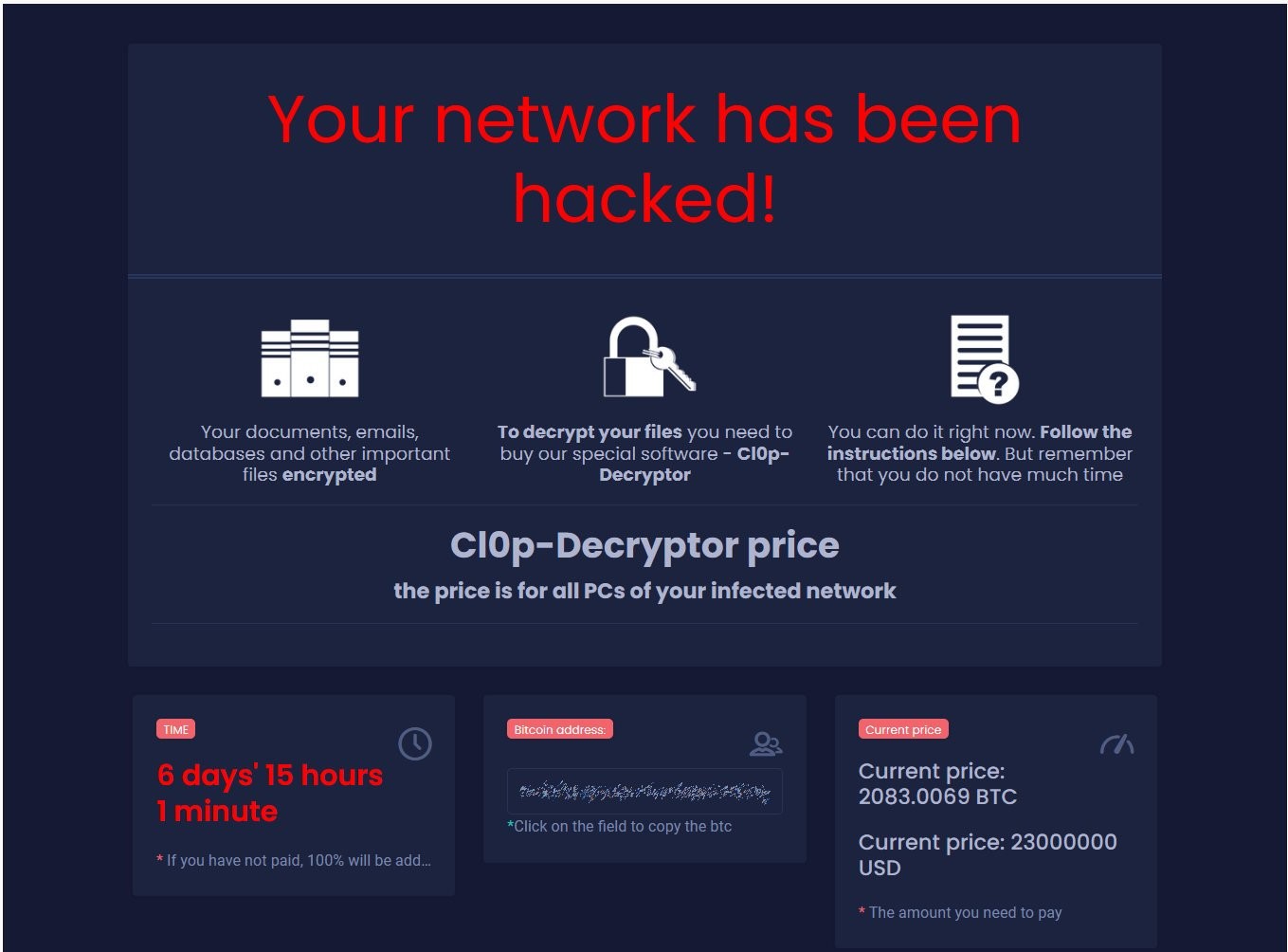
8. CLOP
Clop, sometimes stylized as “Cl0p,” is one of the most widespread ransomware in the past years and has been infamous for infecting high-profile organizations through different industries worldwide. This ransomware is estimated to have huge payouts of about 500 million USD as of November 2021.
9. ALPHV
ALPHV, or black, is another prominent example of one of the modern Ransomware-as-a-Service (Raas) models. ALPHV is a dangerous ransomware that has compromised at least 60 entities worldwide and is written in the RUST programming language, said to be one of the most secure programming languages with excellent performance. This ransomware uses previously compromised user credentials to access the victim’s system.
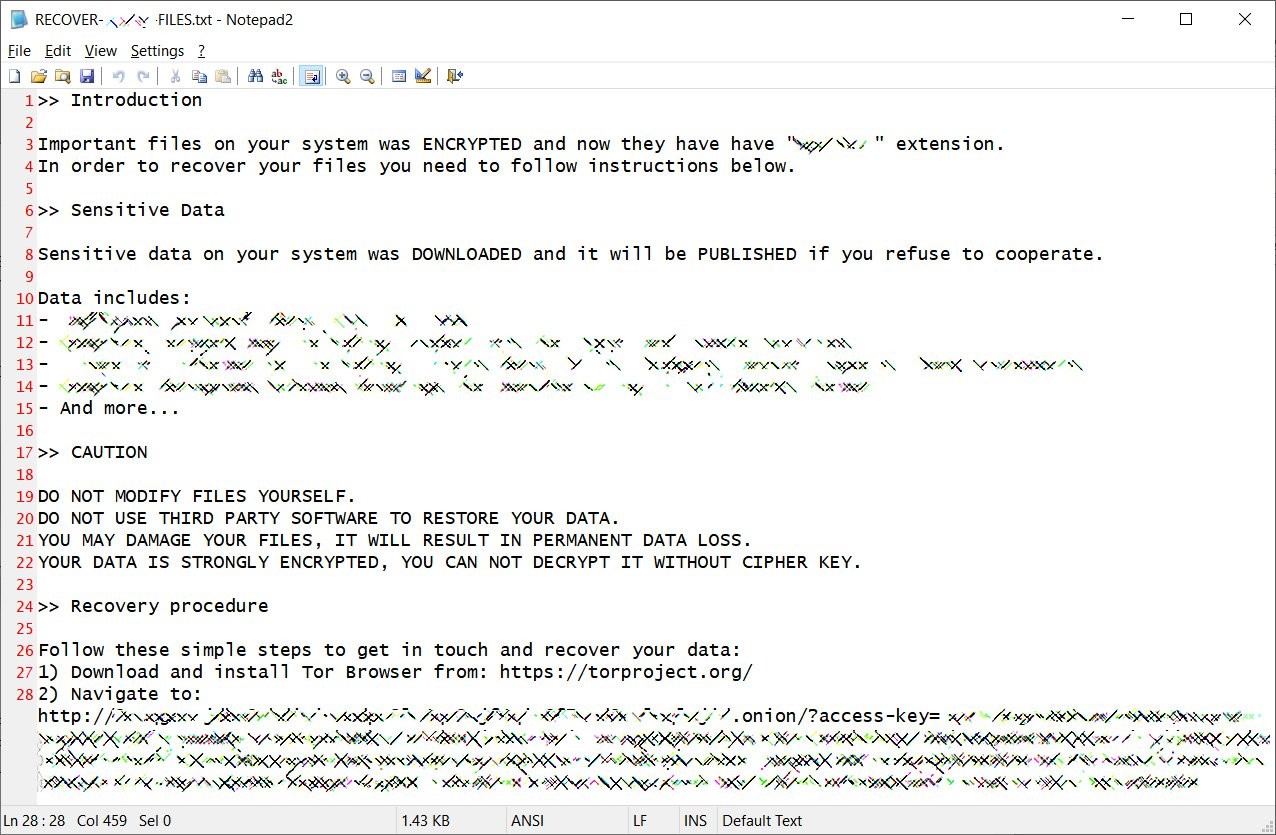
10. Vice Society
Vice Society is another new player in the ransomware market. This group also leverages the same vulnerability as the Magniber Ransomware, and they repackage their ransomware under different names, such as Keq4p, TRX, and MOON. This malware family will be a critical player in the year 2022.



















