Cybersecurity has been a focus since the dot-com boom of the 1990s. Unprecedented occurrences like the COVID-19 epidemic, contested elections, and rising sociopolitical upheaval has led to a boom in cybercrime in recent years. Cybercrime is expected to cost $10.5 trillion by 2025, up 15% from 2015’s $3 trillion.Proactive prevention prevents cyberattacks. Learn about the top cybersecurity dangers in 2023 and how to defend yourself and your organization.
1. Sociology
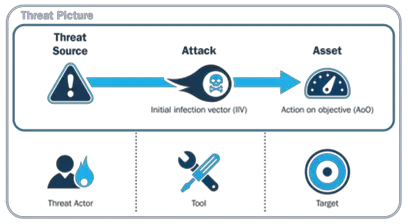
Social engineering is a risky hacking tactic because it exploits human error rather than technological flaws. For example, it’s easier to mislead a human than a security system, making these attacks riskier. For example, 85% of data breaches involve human interaction, according to Verizon’s research.
2023-New:
Social engineering threats like phishing and email impersonation are predicted to evolve in 2023. However, as Bitcoin and other blockchain-based currencies grow in popularity and price, cryptocurrency-related hacks may remain a concern.

2. Second-Party Exposure
Cybercriminals can bypass security mechanisms by attacking third-party networks with privileged access to their primary target.
In 2021, hackers breached 214 million Facebook, Instagram, and Linkedin accounts. The hackers breached a third-party contractor with privileged access to all three organizations’ networks, Socialarks.
2023-New:
Third-party breaches will increase in 2023 as organizations rely more on independent contractors to do jobs traditionally done by full-time workers. Over 50% of businesses are more eager to hire freelancers because of COVID-19, according to a 2021 report. In addition, 96% of firms provide external parties access to crucial systems, giving hackers an unguarded route to company data.

3. Misconfigure
Even intelligent security systems have at least one software installation problem. For example, Rapid7’s 268 external penetration testing found that 80% had exploitable misconfigurations. In testing where the attacker had internal system access, the number of vulnerable configuration errors jumped to 96%.
2023-New:
In 2023, the COVID-19 epidemic, sociopolitical upheavals, and continuous financial stress will likely increase the frequency of careless workplace mistakes, creating additional opportunities for hackers.
81% of workers have experienced mental health concerns due to the epidemic, and 65% feel it has affected their work performance. This stress will worsen a problem. Ponemon Institute claims that half of IT experts don’t know how well their cybersecurity solutions work; therefore, at least half aren’t undertaking regular internal testing and maintenance.

4. Cyber Hygiene
Cyber hygiene” means avoiding unencrypted WiFi networks and using a VPN or multi-factor authentication. Research demonstrates that Americans have poor online hygiene. 60% of organizations maintain passwords by memory, while 42% use sticky notes. However, 54% of IT workers don’t require two-factor authentication for company accounts, and 37% use it for personal accounts. Less than half (45%) of Americans said they would change their password after a data incident.
2023-New:
Due to remote working, weak passwords are being accessed from vulnerable home networks, sticky note passwords, and workers are signing in on personal devices that are more likely to be lost or stolen. Companies and individuals with poor cyber procedures are more in danger than before. IT professionals have poorer cyber hygiene than the general public; for example, 50% of IT employees repeat passwords, compared to 39% of individuals.

5. Cloud Vulnerabilities
According to IBM, cloud vulnerabilities have surged 150% in the last five years. Over 90% of Verizon’s 29,000 evaluated breaches were web app intrusions. Gartner predicts cloud security will expand 41% from $595 million in 2020 to $841 million in 2021. Upticks in novel COVID varieties and breakthrough case rates have rendered an en masse return to the office implausible. This means the threat of cloud security breaches is unlikely to fade in 2023.
2023-New:
New cloud security advances include “Zero Trust” architecture. Zero Trust solutions act as if the network has already been infiltrated, requiring verifications at every step and sign-in instead of giving sustained access to recognized devices or devices within the network perimeter. This security method gained popularity in 2021 and will likely be widely used in 2023.
6. Smartphone vulnerabilities
The COVID-19 pandemic increased mobile device usage. Pandemic experts have urged the widespread deployment of mobile wallets and touchless payment systems to reduce germ transmission.
2023-New:
Increased remote work and BYOD practices have compounded mobile device vulnerabilities. For example, 46% of firms suffered a mobile app security issue in 2021. Cybercriminals are increasingly targeting Mobile Device Management solutions, which are supposed to secure corporate data. Since MDMs are connected to all mobile devices, hackers can attack every employee at once.

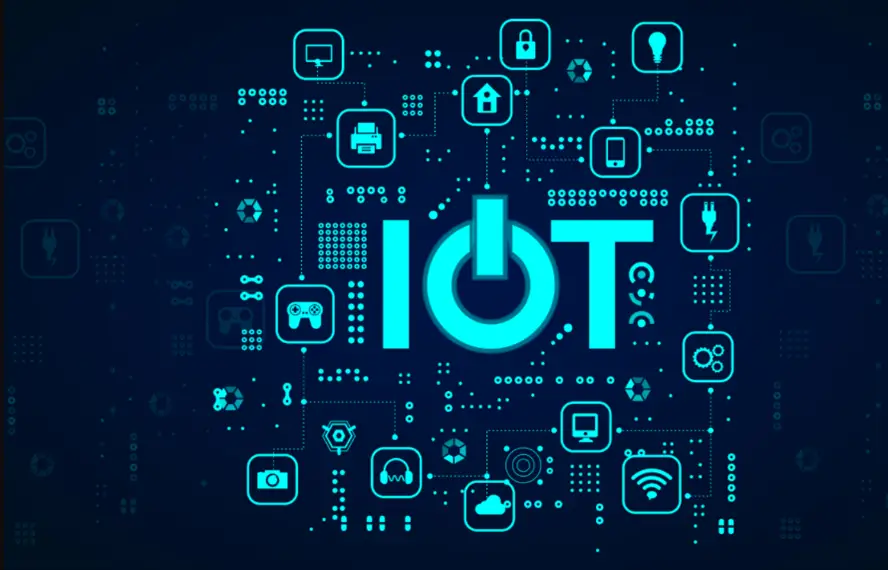
7. IOT
Over a quarter of the American workforce brought their job home after the epidemic, where 70% of households have a smart device. Over 1.5 billion smart or “Internet of Things (IoT)” breaches occurred between January and June 2021. IoT connectivity creates a universe of dangers for hackers, especially given Americans’ poor cyber hygiene. The average smart device gets attacked within five minutes of connecting to the internet, and an intelligent house with several IoT devices may face 12,000 hacking attempts in a week.
2023-New:
Researchers expect the number of intelligent gadgets ordered will double by 2025, generating a more extensive network of access points to penetrate personal and business systems. Over a quarter of enterprise hacks will be IoT-based by 2025, according to experts.
8. Ransomware
The average ransom fee rose from $5,000 to $200,000 between 2018 and 2020, and companies lost income as hackers held system access for ransom. (A ransomware assault averages 21 days of system unavailability.) 66% of 1,263 cybersecurity professionals surveyed in 2021 stated ransomware attacks caused revenue loss. One-third of respondents claimed their organization lost senior leadership by firing or resignation, while 29% said ransomware drove job cuts.
2023-New:
Ransomware has gotten more sophisticated, widespread, and convenient for hackers. Cybercriminals can subscribe to “Ransomware-as-a-Service” suppliers, which offer pre-developed ransomware programs in exchange for a portion of successful ransom payments. In addition, RaaS makes ransomware attacks more economical for small-time crooks. Therefore their number will only rise.

9. Mismanaged Data
Data management involves more than just storage and organization. More than half of the new customer data is never used or examined. Surplus information causes confusion, leaving data exposed to cyberattacks. Data management errors can be as costly as cyberattacks. For example, Aetna was fined $17 million in 2018 for putting sensitive health information in the wrong envelope.
2023-New:
Experts foresee a shift from “big data” toward “right data,” Teams will increasingly rely on automation, which comes with hazards, to sift data. Automated programs are like spiderwebs—a minor incident affects the whole structure. While data processing relies on AI, the rules and settings are designed by humans and prone to error.

10. Insufficient Post-Attack Procedures
After a cyberattack, security must be patched. For example, in a 2021 study of 1,263 cyberattack victims, 80% of those who paid a ransom reported another attack soon after. However, 60% of cyber attacks might have been stopped with a patch, and 39% of firms knew they were susceptible before the attack.
2023-New:
The following year will see the repercussions of 2021’s cyberattacks, which soared due to COVID-19. The 2021 targets’ patch management skills will determine if they’re attacked again in 2023. Subscription-based patch management software is gaining popularity. “Patching-as-a-Service” products offer continual updates and patches, speeding up patching. Automated patching eliminates human-error vulnerabilities.