Testing can never provide 100% assurance of vulnerability identification. The left-alone, stuff can create havoc allowing attackers to perform malicious functions such as access to restricted areas, data theft, remote controlling of browsers, etc. If not tackled vulnerabilities will facilitate various attacks on an application.
Here, We Will Figure Out The Top 10 Vulnerabilities That Every Software Carries.
1. Injection
Injection takes place when the primary aim of the attacker is to alter the program’s code with his work. The attacker’s main target could be the access to confidential data and secure areas while they disguise themselves as a trusted user. Some of the major examples are command injections, SQL injections, and CRLF injections.

2. Broken Authentication
Broken Authentication caused as a result of incorrect implementation of authentication and management calls can enact a feast for the attackers. They can easily disguise themselves into a user’s identity to access restricted data.

3. Sensitive Data Exposure
Sensitive Data Exposure is more prone to APIs that rely upon third parties such as Google Maps for additional services for time-saving. This could happen when the APIs opt for insecure data transmission methods that would attract attackers who target the theft of sensitive information such as passwords and usernames.
4. XML External Entities
XML External Entities come into existence with the successful inclusion of hostile XML content by an attacker due to insecure integrations, code, or dependencies. It can be tackled via powerful scans that are capable of finding harmful third-party components.
5. Broken Access Controls
Broken Access Controls are the replications of improper implementation of restrictions and authentication that easily attract attackers for data theft of sensitive files. Such conditions can lead to unauthorized access to essential data.
6. Security Misconfiguration
Security Misconfiguration could act as an attractive invitation for attackers as it facilitates quick & easy access to confidential data. It can be tackled via dynamic testing to identify such gigantic errors.
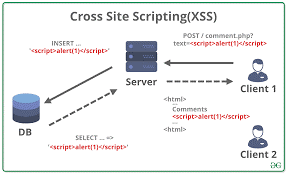
7. Cross-Site Scripting
Cross-Site Scripting is advantageous for attackers that are into APIs & DOM manipulation to facilitate data retrieval via from or send commands. It enacts as a surface widener to give space for threat actors that can easily hijack user accounts, spread trojans, remotely control browsers, and access the history.
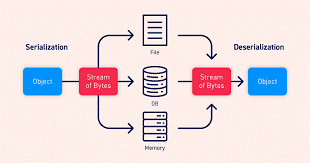
8. Insecure Deserialization
Insecure Deserialization refers to the insecure reveal of data via written disks that enable attackers to execute codes. The most prominent root of this situation is the use of untrusted data for the manipulation of an application.
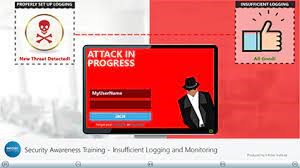
9. Insufficient Logging And Monitoring
Insufficient Logging And Monitoring practices can result in the introduction of the human elements to security risk. These types of flaws enact as an invitation for threat actors because of their slower remediation times that facilitate their attacks before being noticed.
10. Insecure Design
Insecure Design points toward the design flaws caused due to the lack of threat modelling, secure design patterns, secure design principles, and reference architecture.

We would be delighted to hear your opinion & suggestions in the comment box.


















