Hacking can be defined as those activities that compromise our devices and networks through unauthorized access. Hacking in cyber security refers to causing damage or to corrupt systems, gathering information, stealing data and personal information, or causing damage to data-related processes. Hacking in today’s World is a big issue for many, whereas for hackers. it is a considerable profit business. Smart devices such as our phones, laptops, and tablets are most vulnerable to hacking. Webcams and routers can also be hacked, disrupting our data. There are mainly three types of hackers, Grey hat, Black hat, and white hat hackers. These hackers use different techniques to hack your device. In this article, we will discuss the top 10 ways your device can be hacked.
1. Phishing Attacks
Phishing attacks employ fake emails or websites to deceive a user into disclosing personal information, such as login credentials. These websites appear to be legitimate, where a user enters their data, which leads to the data being compromised. Sensitive data, bank account details, and other important data are usually acquired by this means. Phishing can be prevented by never giving details on unsolicited requests, such as on our emails and messages.

2. Malware
Any program that is intended to damage a device or obtain unauthorized access from it is referred to as malware. Malicious URLs, email attachments and software downloads can all be used to spread malware. Malware is one of the biggest threats to your device. It includes viruses, ransomware, spyware, and other unwanted software that gets installed on your device. To prevent this, never download anything from an unreliable source.

3. Social Engineering
Social Engineering is psychologically manipulating a person into disclosing private information or allowing access to a system or network. It involves talking a person into giving away certain information. The hacker may reach the target by mail, phone, or even direct contact to gain information. Multi-factor authorization and verifying the sender’s identity are ways to prevent Social Engineering.

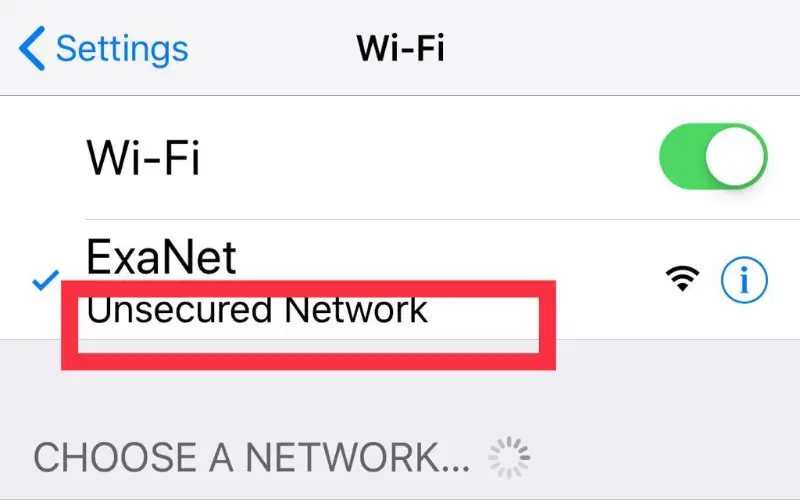
4. Unsecured Wi-fi Networks
Hackers may exploit insecure Wi-Fi networks to eavesdrop on data flows and obtain access to network-connected devices. Unsecured Wi-fi Networks lack cybersecurity to keep your data safe. You need to be careful about what information you are accessing while connected to such Wi-Fi, as your activity can be tracked by hackers.
5. Outdated Software
Older software may include security flaws that hackers can use to enter a system or network without authorization. Old devices in which manufacturers stop to give updates are at risk of being hacked. Regularly updating your apps and using the latest security patch can help prevent the risk of being hacked.

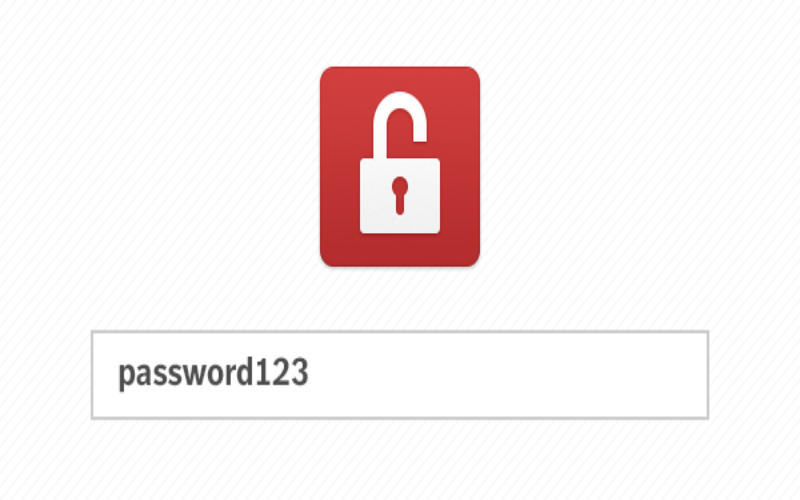
6. Weak Passwords
Hackers can get unauthorized access to devices and networks by quickly guessing weak passwords. This is why it is always recommended to use strong passwords containing numbers, upper case, and lower case letters and symbols. A short and common password can easily be guessed by hackers leading to vulnerability.
7. Bluetooth Vulnerabilities
Bluetooth can be accessed by hackers to gain unauthorized data access to various devices. Modifying and reading data wirelessly between two devices is a common way of Bluetooth hacking. The newer versions of Bluetooth now come with encryption which helps to protect our data to some extent.

8. Fake Apps
False applications can be made to seem like genuine programs, but they are harmful programs intended to access a device or network without authorization. Apps that we use daily, such as file manager or photos apps, are duplicated and may even get installed on your device unknowingly. Always use legitimate websites and platforms to download apps to prevent this.

9. Physical Access
A hacker may be able to install malware or obtain unauthorized access to sensitive data if they have physical access to the target device. If you give your device to an unknown person, they may tend to download malware and twitch specific settings making your phone vulnerable. Always use security apps, and don’t hand over your device to someone unknown.

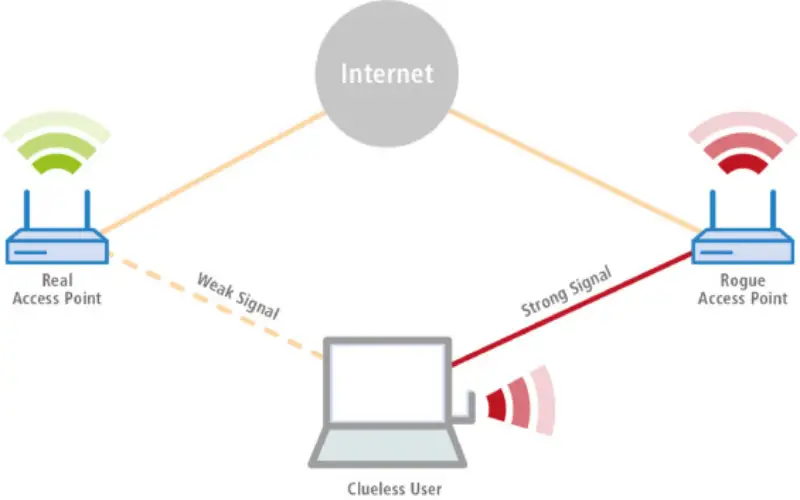
10. Rogue Access Points
Hackers can set up rogue access points to imitate legal Wi-Fi networks and access devices and networks. It is a wireless access point that is installed on a network without authorization from the administrator. Mobile devices connected via USB tend to be vulnerable to such activities. An attacker can intercept the data flowing through the port, for example in the case of ethernet.