Hacking has become riskier, and legal action is now being taken. Many crimes are committed under the guise of hacking and must be prevented. Hacking is the act of detecting and exploiting flaws in computer systems and/or computer networks. There are several hacking strategies, including as phishing and email spoofing. There are three sorts of hackers: white hat hackers, black hat hackers, and grey hat hackers.
1. SQL Injection
SQL Injection is a well-known and often utilized website hacking technique since SQL is currently used for database interaction. The SQL language is used by database management systems like SQLite, Microsoft SQL Server, MySQL, PostgreSQL, and others to create, read, edit, and remove database records. An attacker would inject SQL code into a web form and try to get the server to execute it. It can be used to gain illegal access to a program or to delete, change, or add new database records. In reality, there are several tools available to perform a SQL injection attack.

2. JavaSnoop
JavaSnoop is a tool for hacking java applications. JavaSnoop is a tool that intercepts methods, alter data or checks the security of the application. JavaSnoop accomplishes this by letting you to link to an existing process (much like a debugger) and immediately begin interfering with method calls, running custom code, or simply watching what’s going on the system.

3. Java Applet DNS Rebinding
Allowing random cross-origin queries is recognized to be exceedingly risky. As a result, most current browsers reject these requests. A pair of Java applets redirect a browser to two attacker-controlled Web sites, causing the browser to skip its DNS cache and therefore making it vulnerable. This approach enables attackers’ programs to gain access; to private resources using malicious hostnames while avoiding the same-origin restriction.

4. Cross Site Scripting (XSS)
Cross-Site Scripting is another well-known tactic for attacking websites and stealing information. In this strategy, the hacker inserts malicious JavaScript code as well as hyperlinks on the user end. When the user clicks on the link, JavaScript code is triggered, which can result in account theft, session hijacking, and some personal data theft. It is widespread on social networking platforms and web forums and does not necessitate a user being signed in.
5. Cookie Theft
Cookie Theft is when a third party steals unprotected session information and employs it to imitate the genuine user, this is referred to as cookie theft. It enables a hacker to steal our confidential data. Cookies; typically found in web browsers that; store user credentials such as usernames, passwords, and browsing history, among several other things. Because these data get saved in the form of text, it is quite easy to be hacked or stolen by a hacker.

6. Phishing
Phishing is a technique in which an attacker mimics the genuine website and then convinces the victim to use the false webpage rather than the genuine one. When; you submit your credentials on that bogus website, your private information is compromised. The information is sent straight to the hacker, who might then misuse the sensitive data. The hacker uses this strategy to gain payment information like credit card numbers or personal information such as login credentials to crucial accounts and websites.

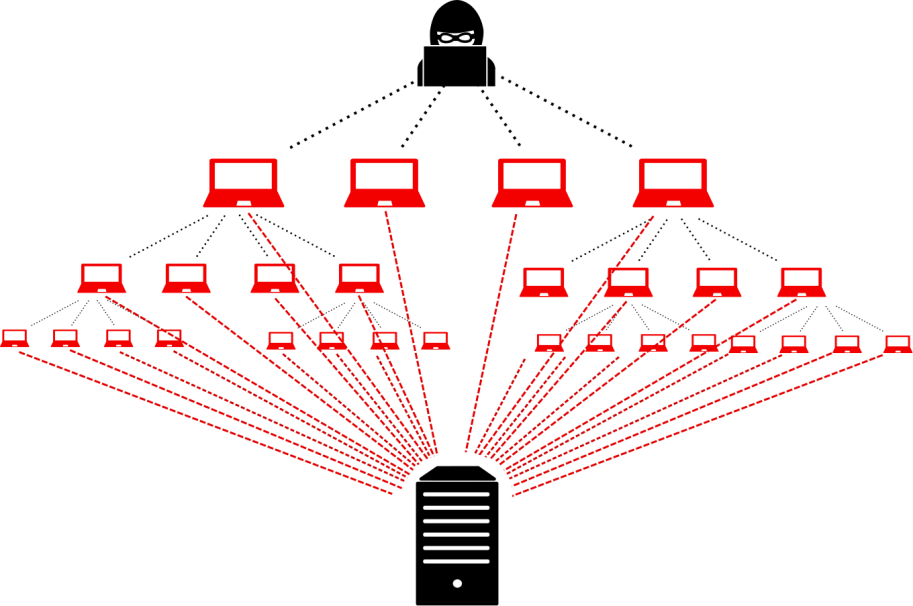
7. DDos Attack
DDoS is Distributed Denial of Service. This method is used to bring down the website by server crashing. With the use of zombie machines or botnets, attackers overwhelm the servers of the targeted website. The servers fail as a result of this overtaxing their resources. In certain instances, this approach was also utilized to steal user information by stalling user forms.
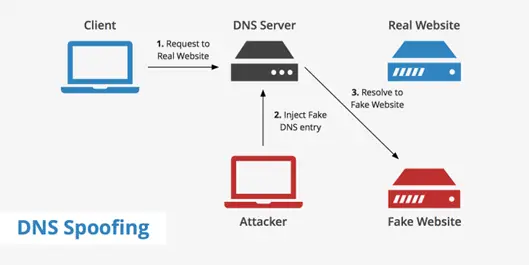
8. DNS Spoofing
DNS Spoofing is also called DNS Cache Poisoning.As a type of computer security attack, DNS spoofing involves introducing erroneous Domain Name System data into the DNS Resolver’s cache so that the name returns an inaccurate result record. Thus it redirects the user to fake website and ask for login credentials and personal information. Thus data theft occur. This type of attack may quickly spread from one DNS server to another, contaminating every DNS server in its route.
9. Brute Force
In this strategy, the hacker attempts various password combinations to get access to the user’s account until one of the password combinations matches. This approach appears to be simple to implement, but it needs massive computational power. Longer passwords are more difficult to guess using the brute force approach. The assailant occasionally uses dictionaries as well.

10. ClickJacking
A frequent click-hijacking technique called clickjacking is employed by video streaming websites to deceive you into clicking hidden links without realizing it. The hyperlink is disguised behind a video play button, and when clicked, it displays advertisements or links to dangerous websites for data theft. An attack uses this cunning website hacking tactic to deceive you into clicking a link you weren’t aware of. While they may not be pursuing your personal information, they are after the ‘fraudulent’ ad clicks that make them money.