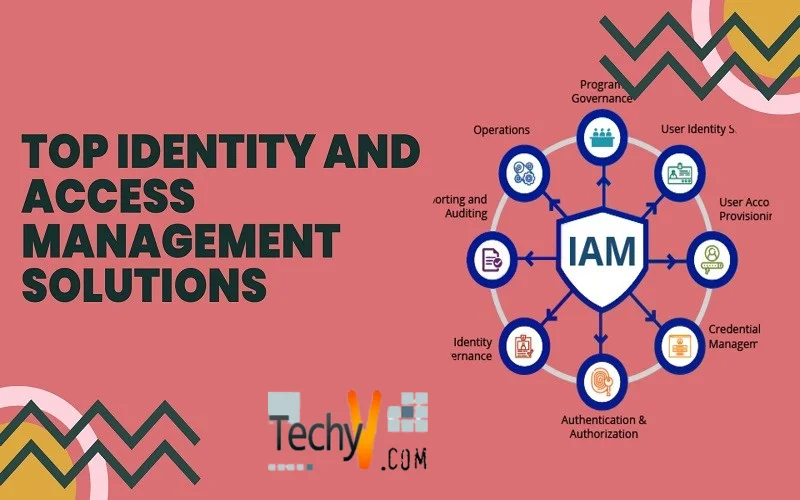
Recently, there has been a substantial rise in cyber attacks such as credential thefts and account takeover attacks. It is the duty of of IT teams to carefully monitor and reduce potential risks associated with cyber attacks by implementing a robust Identity and Access Management solution.
An Identity Access Management (IAM) solution ensures the safety of your credentials and helps in identifying potential vulnerabilities. An IAM solution ensures that only authorized users can access your data and system. The tool supports IT team in managing user identity across multiple systems and applications by providing a centralized solution for access control, de-provisioning, and user provisioning.
An efficient IAM solution helps in safeguarding an organization’s valuable data, ensure regulatory compliance, minimize costs, and enhances user experiences. As per the analysis by Fortune Business Insights, there will be a considerable rise in demand for ‘just-in-time’ privileged access management solutions by 2025. A efficient IAM solution ensures that only a right person can access the company’s system and vital information.
Users can log in and access multiple locations in a single sign-on, leading to improved efficiency and easy management of several passwords. With multi-factor authentication, users are required to provide two or more authentication factors like password or OTP to minimize the risk of unauthorized access. The tool also offers detailed audit reports to monitor user activities, track changes, and present regulatory compliance needed by auditors. In this article, you will discover the top 10 identity and access management solutions suitable for your organization.
1. CyberArk
CyberArk’s identity and access management solution protects your organization from cyberattacks. It ensures that users get access to the right information quickly. Users can access different applications using one single password. With its innovative privileged access management capabilities, users can easily monitor and secure access to privileged accounts and reduce the risk of data breaches. CyberArk provides a secured password vault to store sensitive data in an encrypted form.

2. Zluri
Zluri offers a centralized platform to control and manage access rights within your organization. Zluri ensures that your IT teams have complete control over the business critical assets and data. With a user-friendly dashboard, the tool streamlines the onboarding and offboarding process. Zluri supports role-based access control and ensures users the access to information needed for their unique job roles. It offers integration with various SaaS and on-premise applications. Through Zluri’s self-service portal, employees can access essential apps and manage their accounts without IT intervention.

3. Azure Active Directory
Microsoft’s Azure Active Directory is a cloud-based identity and access management solution that is the foundation for Office 365 applications. Azure Active Directory incorporates machine learning to identify stolen credentials and suspicious login attempts. User credentials are secured using conditional access policies. Azure IAM integrates with other user applications such as Jive and Workday to secure user access to data. The tool enhances user experience and productivity by simplifying the login process and reducing the time needed to manage passwords.
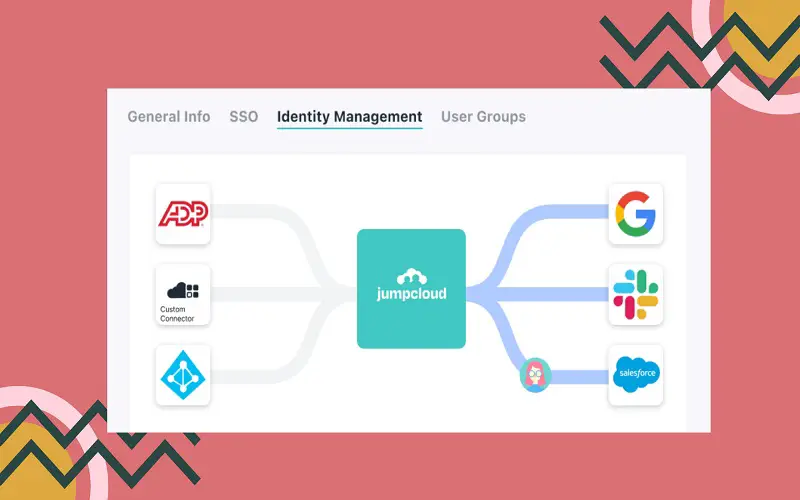
4. JumpCloud
JumpCloud offers comprehensive cloud-based solutions enabling users to safely access various resources, both on-site and in the cloud. It’s an open directory platform that boasts a range of directory services, SSO, privilege account management, and multi-factor authentication. JumpCloud virtually connects an employee to resources and secures their devices remotely. Administrators can quickly provision users and devices worldwide through an automated process from a single web interface.
5. IS Decisions
IS Decisions IAM solution offers services to secure Windows Active Directory and cloud environments. UserLock is the access management solution for Active Directory identities that unifies the power of MFA, SSO, and session management to secure user access to corporate resources and cloud-based apps. Companies can prove compliance with data protection standards using the UserLock. Even IT admins can establish multi-factor authentication across various apps with the help of UserLock. The platform utilizes authenticator apps and hardware tokens, such as Token2 and YubiKey to authenticate user identity.

6. OneLogin
OneLogin streamlines user experience by enabling them to access all the applications using a single set of password. Their onboarding and offboarding process for employees is straightforward. With a single click, users are granted or revoked access. OneLogin’s comprehensive reporting and auditing features enables organization’s to monitor user activities, track login attempts, and create a detailed report on their security postures. It helps in avoiding the risk of data breaches and boosts productivity. The tool seamlessly integrates with an organization’s directory services to simplify access management and minimize errors.

7. ForgeRock
ForgeRock is an identity and access management solution powered by AI. ForgeRock ensures uniform password guidelines across various applications, devices, and IoT objects. Through its user dashboard, users can easily manage credentials and privacy preferences across multiple websites. ForgeRock utilizes AI technology to determine and analyze user activity and detect blind spots. The data is stored securely in the cloud, making it easy to access from multiple devices and over the IoT network.

8. Ping Identity
Ping Identity streamlines user access to various applications using a single credential from a central dashboard. Users are not required to maintain multiple credentials for accessing different applications. Ping Identity ensures uniform identity management and access control over the entire IT system by seamlessly integrating with popular cloud platforms. It offers additional protection using multi-factor authentication. Its adaptive authentication system analyzes each login activity to assign risk levels.
9. IBM Cloud
IBM Cloud’s IAM solution utilizes AI technology and deep analytics to automate various identity management tasks, including modifying user access and tracking unusual patterns in user behavior. IBM Cloud seamlessly connects with popular cloud platforms to expand security measures to cloud-based applications and resources. The Single Sign-On feature simplifies the login process and reduces the risk of password breaches. IBM Cloud provides a centralized management solution to ensure that users have the right level of access to resources as per their needs.

10. Okta
Okta offers an enterprise-level solution for cloud and a variety of on-site applications. The platform provides solutions that helps businesses to efficiently manage their employees identity. Okta streamlines business processes by enabling the creation of customized applications and providing employees with a uniform password for all corporate accounts. With its comprehensive dashboard, admins can effortlessly manage internal and external users and view comprehensive reports.