Nowadays, smartphones have become an essential part of our everyday life; without them, we can’t imagine our future because they have made everything effortless, from calling our loved ones to other things such as texting, web browsing, playing games, and many more things. As we all know, everything has pros and cons; so, in the case of smartphones, there are also some pros or so-called threats, which are described below.
10. Poor Cyber Hygiene
Proper cyber hygiene is essential to maintain reasonable data security. Many smartphone users continue to use weak passwords, share data with friends and colleagues, and also do not do proper updates on their operating systems and apps.

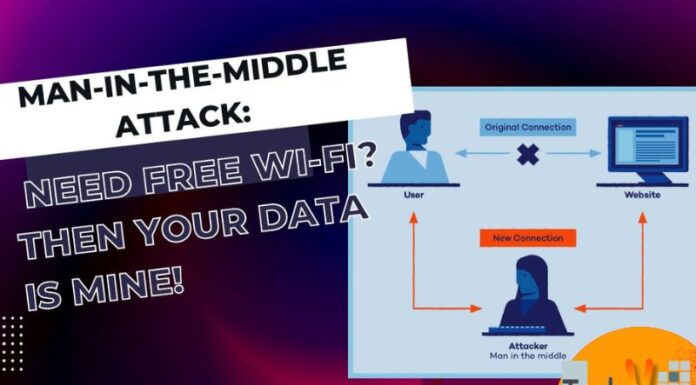
9. Network Spoofing
Network spoofing is when hackers create fake access points- connections that exactly look like trusted wifi networks and are commonly used by hackers mainly in high-traffic public locations such as airports, schools, colleges, and restaurants. In other cases, hackers used to provide setup a procedure to access these free wifi networks in which people commonly use their email and password to log in to that network, and this causes a significant threat to their data security by which attackers fetch their email login, e-commerce, and other pieces of information.
8. Application With Weak Security
With poor security standards, many smartphone applications can make your information vulnerable to various malicious practitioners. The developers of the apps might use weak encryption that can be easily hacked or unintentionally share digital tokens that allow hackers to impersonate real people online.

7. Out-Dated Device
Regular update on smartphones is the key to protecting them from various type of malware and other cyberattacks. Smartphones that are too old to receive security updates should be replaced; even if it seems to run still, there is a risk in using an old phone that hasn’t received the latest security updates.

6. Ransomware
Ransomware is a type of malware that prevents access from the files or the data of any organization to its users and demands payments to gain access. This is the most prominent method of cyberattackers because most users think that their file is locked by the system, but despite that, the leading cause of it is ransomware.

5. Phishing Attacks
Phishing attacks are the practice of sending all fraudulent communications that look from the trusted sender/source, usually done through email. The main goal of these types of attacks is to steal sensitive data like a credit card or login credentials or to install malware into the victim’s phone.

4. Poor Password
Almost all smartphone users create passwords of their name, birthday, and pet names on their own; this causes big turbulence in their data security and can cause a breach in by another person who knows them and is easily accessible with a little bit of effort. Also, many people create numbers for passwords and simple letters, which are also examples of poor password habits.

3. Spywares
Spyware is a type of malicious software that is installed on a user’s smartphone without his consent. With the help of spyware, anyone can invade the device, steal the user’s private and confidential data, and send various types of data to advertisers, data firms, and so on.

2. Open Wifi Networks
Most people love to use free/open wifi networks instead of using their data pack and, this creates a golden chance for cybercriminals to sneak into our smartphones and steal our precious data. Also, by this, they can manipulate many things; for example- the user wants to use their banking website, so with the help of open wifi the cybercriminal can get his bank details and so on.

1. Data Leakage
The primary aspect of data leakage is web browsing; it is so because any smartphone user almost does all essential things such as web searches, online shopping, reading, and many more things. The web browser stores all things related to our inquiries, passwords, and login credentials which are convenient for cyber criminals to steal data from one place.