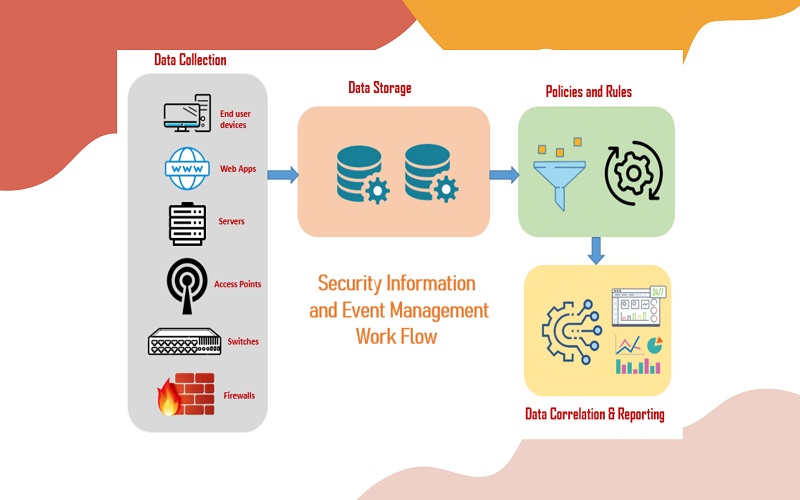
The Security Information and Event Management, also known as SIEM is a security tool that adopts a use case framework to identify and detect security threats. The use case framework integrates with the company’s security and compliance protocols, to ensure solid detection capabilities that are consistent with the organization’s threat landscape. Implementing SIEM successfully involves utilizing a set of use cases that clearly defines an organization’s security threats and solutions to overcome them.
The need for early identification of data breaches and attacks has created a demand for the implementing an advanced SIEM system. An advanced SIEM system collects and store the data, and automatically respond to security threats. Organizations must focus on three essential pillars while implementing a comprehensive SIEM use case (insight, data, and analytics).
It is imperative for businesses to regularly evaluate the use cases based on dynamic risk landscape and business needs. Each use case requires a varying amount of effort, based on the size and maturity of the organization. They need to be segregated into hierarchical families to ensure compliance, threat detection, and business-level application. Therefore, businesses should pay attention while developing the required use cases. Try to use varied levels of granularity to outline use case scenarios within your organization.
SIEM’s “user activity monitoring system” enables easy access control and offers reports on policy breaches and suspicious activities. It has a better incident response rate that can automate workflows efficiently.
Let us check the top 10 use cases of SIEM that may help businesses improve their security defences.
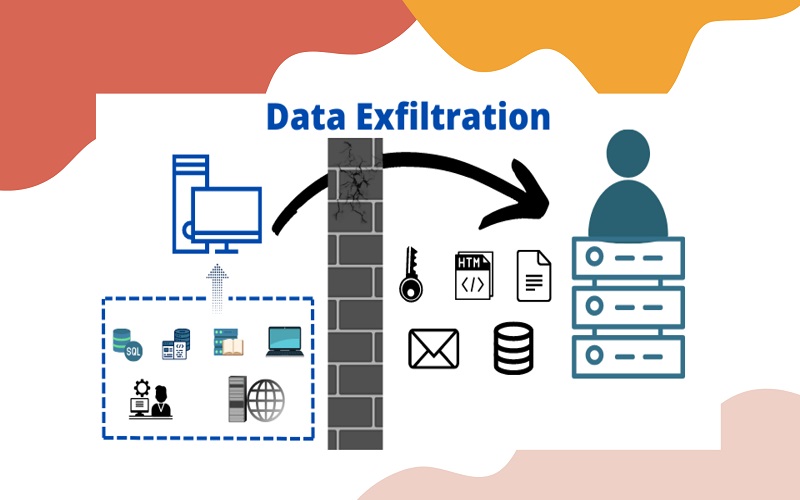
1. Detection And Prevention Of Data Exfiltration
When the data is transferred from a company’s storage system to a flash drive, IT servers, or mobile devices by hackers without the proper authorization or permission, it is known as data exfiltration. Certain specific data are precious for the company. If data is transferred in an unauthorized way, then it might cause severe threats to the business’s privacy and security. Using an event correlation motor, an efficient SIEM system can quickly detect suspicious activities by the attackers. It links the network traffic with a threat intelligence service to identify malware that communicates directly with external attackers.
2. Payment Card Industry Compliance
SIEM supports business organizations with PCI compliance. It helps detect unauthorized network connections and looks for insecure protocols and servers. It regularly monitors and checks for events that may cause changes in user credentials. It help gather security logs that meet the PCI logging standards and regularly audits them for PCI reporting.

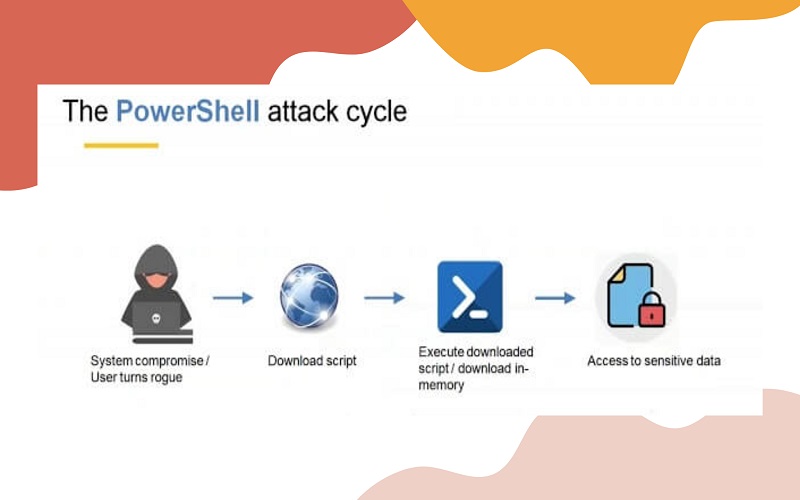
3. Detection Of PowerShell Attacks
PowerShell is a Windows pre-installed command-line tool installed across multiple systems. The system administrators utilize PowerShell to automate a wide range of tasks. But, sometimes these software pose security threats to business’s privacy. SIEM is capable of detecting PowerShell attacks efficiently by implementing correlation processes. The platform utilizes control, process creation, and EDR logs to detect cyber threats.
4. Health Information Compliance
SIEM ensures compliance with health insurance regulations. The software helps organizations to discover new IT assets, identify systems at risk, and control access to business critical files. It checks for login attempts and modification of the user’s account. SIEM regularly monitors the modification of health information and changes in data policies. It can also inspect for unauthorized communications and attempts to alter health information.
5. Detection Of VPN Attacks
Companies utilize VPNs to facilitate easy communication among the employees. Cyber attackers misuse VPNs to obtain user information and access business’s sensitive and valuable data. SIEM system constantly monitors all the VPN condensers to identify users and IP address associated with each new connection request. It correlates IP addresses with geographical location coordinates by utilizing the services of a third party.
6. Ensuring GDPR Compliance
Utilizing SIEM solutions for GDPR compliance ensures compliance with all the clauses of the law. A robust SIEM system supports the organization in meeting the GDPR requirement and offer services including detailed investigation, threat detection, compliance reports, and log data management. An efficient SIEM system promotes data transparency and comprehensive analysis of data processing.

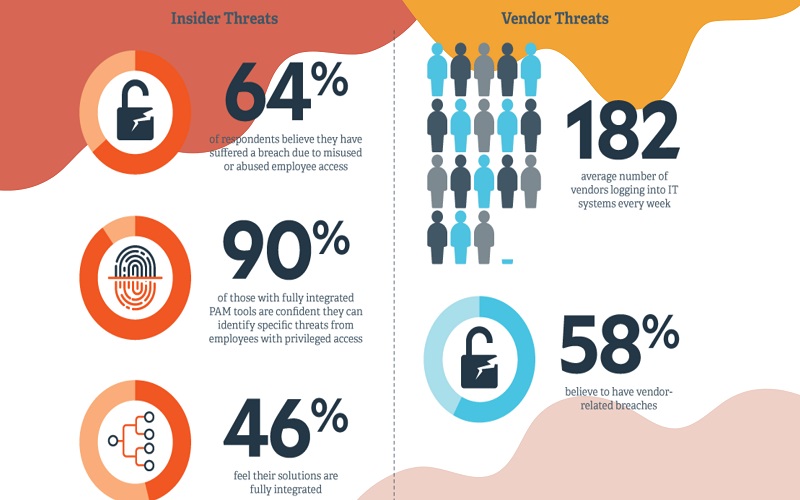
7. Prevention Of Privileged Access Abuse
Privileged Access Abuse arises when individuals with IT access engage in undesirable activities. They are offered more power than they need for their job and it is the second largest cause of security incidents. SIEM solutions can help prevent Privileged Access Abuse. An efficient SIEM system can identify suspicious access to any sensitive data. It alerts the organization if any suspicious activity is detected in terminated user account. It also aids against third-party violations by consistently monitoring the activities of external vendors and third parties with access to business-critical systems.
8. Detection Of Zero-Day Attacks
In zero-day attacks, cybercriminals misuse security flaws in an application or program’s source code to attack the system. SIEM solutions can detect zero-day attacks with the help of correlation rules and cyber threat intelligence. By implementing dashboards, alerts, and reports, the system empowers IT administrators to easily track security incidents and paths.

9. Advanced Security Threats Detection
SIEM alerts the security systems by delivering actionable alerts that offer context and data. It identifies anomalies in IT systems by utilizing correlations and behavioral analytics. It helps businesses to organize data around new timelines and systems. It also conducts historical research to identify similar data attack patterns. SIEM aligns threat intelligence with security data to detect attacks in IT systems. It helps analysts frame hypotheses based on known risks.
10. Improving The Efficiency Of The IT Security Team
SIEM solutions focus on improving the efficiency of the IT security team by leveraging correlation processes. AI and machine learning technology help security teams to accelerate search and reporting capabilities. It enables IT security teams to focus their attention on highly critical issues by upgrading the existing reactive security systems into a proactive system. SIEM’s delegation feature allows you to assign authorities based on the duties of the staff.



















