Network security is a phrase that labels the security implements, strategies, and security plans aimed to check, avoid and take action on unofficial network interruption while also guarding digital properties. To defend against these hazards and protect your corporation from possibly millions of bucks in data damage, you require authentic, strong web security and network prominence. Following is a list of a few of the best network security tools.
1. Access Control
Network access control is the act of detaining unsanctioned operators and devices from a remote network. Protected network access control grants extra heights of guard around separate parts of the web after a user has secured access, certifying application security. Some network access control solutions might contain compatible security controls, for instance, encoding and amplified network visibility. If threat executors cannot get into your network, the amount of impairment they will be capable of will reduce tremendously.

2. Wireshark
Wireshark is a network protocol evaluator or an application that seizes packets from a web link, such as from your processor to your home office or the Internet. A ‘packet’ is a term for a separate part of data in a particular Ethernet network. Wireshark displays a summary of the immediate network. For safety and device supply purposes, many favor Tcpdump, yet Wireshark continues to be the most popular packet sniffer. Cybersecurity pros often use it to track contacts, consider the contents of suspicious network deals and recognize surges of network passage.
3. Anti-Malware Software
An anti-malware is a software package that defends the processor from malware such as spyware, adware, and worms. It scrutinizes the system for all forms of malicious programs that manage to influence the software. An anti-malware database is one of the top tackles to keep the computer and private data secure. An anti-malware program generally comprehends complex malware shield and sandboxing technology. Characteristics may contrast varying on the software. It is an advanced safety feature that terminates malware immediately when it appears on the system.

4. Application Security
Application security defines safety measures at the application level that aspire to avert information or encryption within the application from being slipped or captured. It includes the safekeeping deliberations that occur during application enhancement and plan, but it also comprises schemes and methods to shield applications after they get installed. There is a growing burden and encouragement on guaranteeing safety at the network base and within applications themselves.

5. Email Security
Aggressors frequently use emails to spread malware, unsolicited mail, and phishing strikes. Attackers use deceiving mails to tempt receivers to share confidential material, uncluttered attachments, or click on hyperlinks that invest malware on the target device. Email is also a usual access point for invaders looking to obtain a grip in an initiative network and attain treasured establishment information. An email programming solution cuts the dangers connected with supervisory damages, data harm, and enterprise strategy abuses.

6. Aircrack
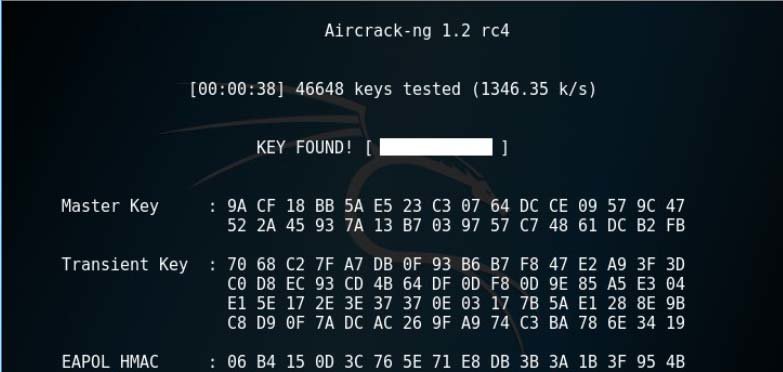
Aircrack-ng is a tool that arrives pre-installed in Kali Linux and is used for Wi-Fi system safekeeping and managing. Aircrack is an all-in-one package sniffer, WEP and WPA/WPA2 cracker, dissecting tool, and a mess arresting implement. It is a program used for Wi-Fi hacking. It supports catching the package and delivering the muddles out of them. It even breaks the muddles by several outbreaks like dictionary strikes. It sustains almost all the newest radio interfaces.
7. Firewalls
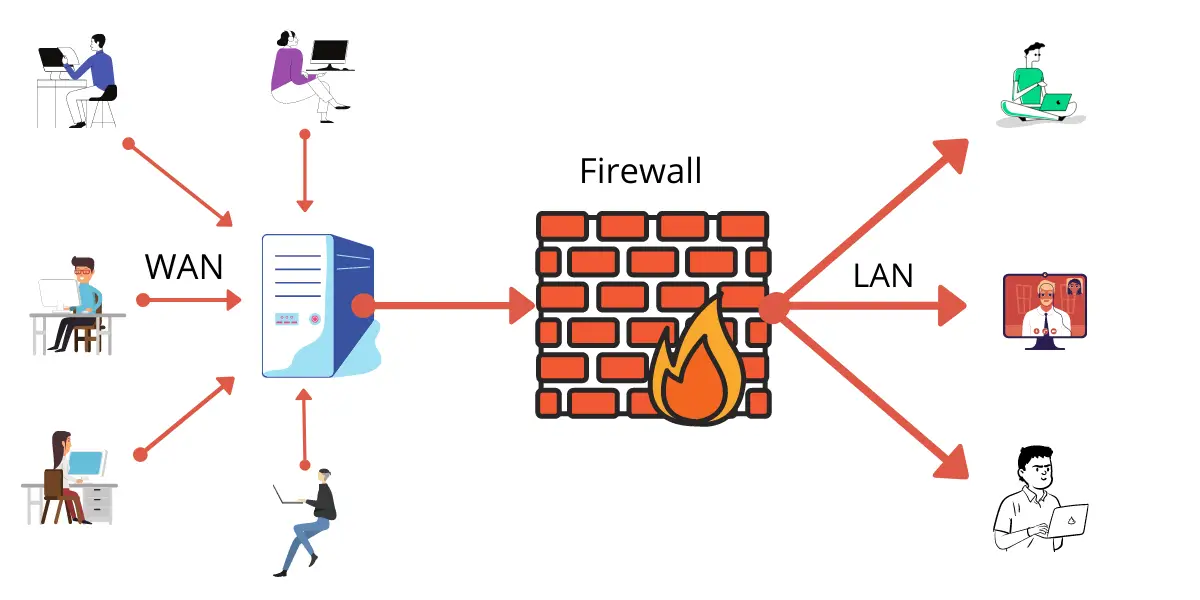
A Firewall is a network safety tool that supervises and categorizes inbound and outbound system circulation centered on an administration’s formerly recognized insurance procedures. The aim of a firewall is to permit non- pressuring traffic in and to hold unsafe traffic out. They can establish guidelines to protect your connections and perform swift valuations to sense offensive or distrustful movements, like malware, and shut it down. Firewalls run like gates we use to lock the boundaries amid your web and cyberspace.
8. Web Security
Web security states the defensive protocols and conventions that establishments approved to guard the corporation from cyber convicts and threats that use the network. Web security is significant for corporate steadiness and shielding information, operators, and businesses from hazards. The certainty is that cunning assailants might be capable enough to discover faults even in an equitably vigorous protected setting, so we recommend a complete safekeeping approach.

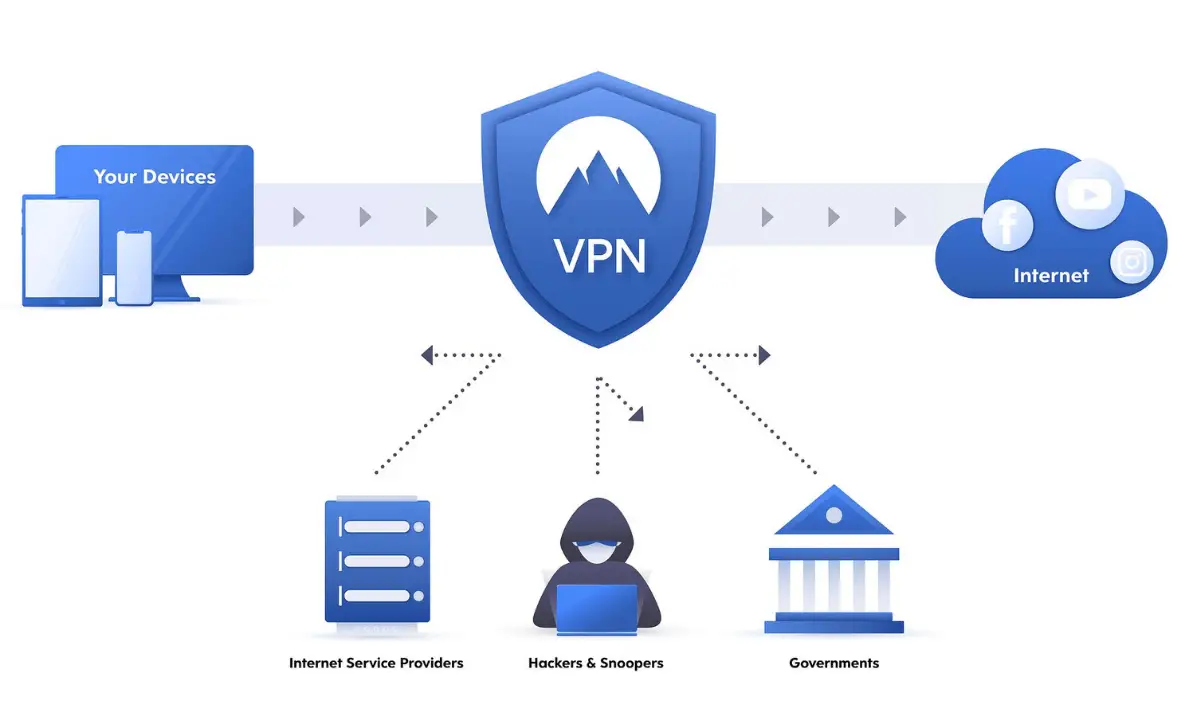
9. Virtual Private Network (VPN)
A virtual private network (VPN) is an encoded connection over the Internet from a device to a system. The encoded link makes sure that complex data conveys securely. It avoids unsanctioned bodies from spying on the transfer and lets the operator lead work distantly. People use VPN technology broadly in commercial situations. Due to the encryption of the circulation between the device and the endpoint network, interchange remains remote as it travels. Even smartphones and tablets can link via a VPN.
10. Wireless Security
Wireless network security is the course of scheming, executing, and certifying safety on a wireless computer system. It is a subdivision of network security that increases protection for a wireless computer network. Firm wireless security actions are essential to confirm that threat attackers are not securing access. Furthermore, wireless interference recognition and anticipation arrangements also empower the protection of a wireless link by notifying the wireless web overseer in case of a security break.