Use of Cryptography in Security
As we know in today’s world, network security is a big issue. Here we will try to understand one type of network security solution i.e. Cryptography. Cryptography, invented since Greek times, means “Secret writing”. It is a skill to hide the message in such a way that it will become secure and protected to attacks.

The above figure shows the working of Cryptography. The message to be encrypted is known as plain text. It is the original message before transformation. The result of the Encryption process is known as Cipher Text. Encryption and Decryption Algorithm are referred as Cipher. Key is a number or set of numbers operated by a Cipher. The Art of breaking cipher is known as cryptanalysis and the art of devising them is known as cryptology.
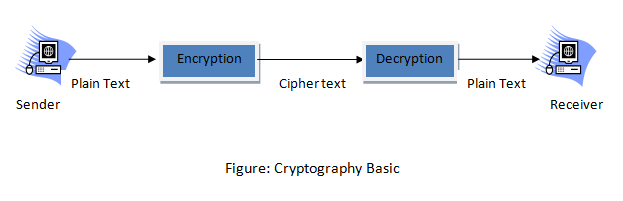
Sender sends a message using Plain text. After that, message is encrypted and a key is added, so it becomes Cipher text and goes to receiver side. At the Receiver side, Decryption algorithm converts Cipher text to plain text and thus provides original data.
The cryptography Algorithm is divided into two groups.
- Symmetric key Cryptography Algorithm
- Asymmetric key Cryptography Algorithm
Symmetric key Cryptography Algorithm :
In this type of cryptography Algorithm, sender and receiver use same secret key. Sender uses this key and encryption algorithm encrypts the data and receiver uses this same key and decryption algorithm decrypts the data.
There are two types of algorithm to be used. One is traditional algorithm i.e. character oriented and second is modern algorithm i.e. bit oriented.
- In character oriented algorithm, one letter is replaced with another. For example if plain text contains alphabet B, it may be replaced by alphabet E. Likewise if digit 0 may be replaced by digit 3. In mono alphabetic Cipher, which is a type of Substitution cipher, one character in plain text is always replaced with another character in the whole document regardless of its position. Suppose C is replaced by G then C in the whole text is replaced by G. Sentence like COW CAT will become GOW GAT. A Polyalphabetic cipher is also a type of substitution Cipher in which one character or digit is changed to another character or digit according to its position. For example, Character A is changed to D in beginning but it might be change to H in the middle.
- Another character oriented algorithm used is transposing cipher. In this, the location of letters is changed. A character in first position in plain text might be appearing in sixth position in cipher text. A key is used for mapping the position of symbols in plain text and cipher text.
- Now second is the Bit Oriented Cipher which is a modern cipher. We require modern cipher because we transfer not only plain text but also video, audio and image files. Some examples of modern cipher are XOR cipher, Rotation Cipher, modern round cipher etc.
- The advantage of symmetric key Algorithm is efficiency and easy implementation in hardware. And a disadvantage is that key management is difficult.
Asymmetric Key Cryptography (Public key cryptography):
- Public key cryptography can be implemented with two keys i.e. public key and private key. The public key is use to encrypt the data and private key to decrypt the data.
- One common cipher used in public key cryptography is RSA (Rivest, Shamir and Adleman). RSA chooses “n” to be the product of two primes “p” and “q”. Another is Diffie Hellman method which provides one time assembly key for two parties.
So this is the way of using cryptography for securing data.