DNS explained 2000,2003 & 2008 Active Directory
History
Contrary to NT that had flat user management service, active directory was introduced to provide true directory services.Ten years after its introduction in the 1990’s, it did not get the expected popularity and was thus embedded as a part of the Windows 2000 Server operating system. The management flexibility of active directory helped gain popularity and a time came when the Microsoft programmers had to strive to introduce its newer version in 2003, and later in 2008.

LDAP
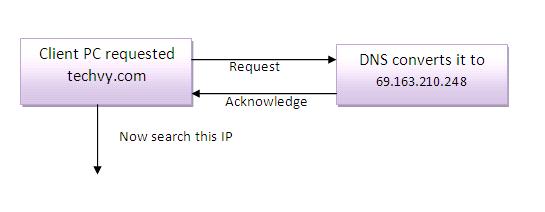
Active directory can be called as a modified version of Lightweight Directory Access Protocol LDAP that was a protocol prepared by the University of Michigan for modifying and querying the directory services.
It was developed with the idea to build a directory that stores information about people and objects such as computers, people or users, domains, applications and security access permissions, etc.
Windows Server 2003 Active Directory
Windows 2003 server organizes the objects and their available attributes on the network into a hierarchical representation. The administrator can easily and more precisely control the components of the network like computers, users, shared drives and folders, printers, etc. Forests, trees, domains, organizational units and individual objects are combined to form this logical representation of the network. The physical structure of the network topology has nothing to do with this structure.
Active Directory tools
If a network is desired to run in a Windows based environment, application of active directory is a must. This is because the users make a large number of changes in the active directory daily; if the resources are not properly allocated to them, the network will collapse. To avoid such a predicament, it is needed to keep a watch on the active directory with the help of its management tools.
It is a common phenomenon that whenever there are a large number of options available in a procedure, it becomes complex.However, Microsoft has designed some features that facilitate its complex structure to be used in a friendly way.e.g. Softerra Adaxes is a flexible and efficient AD management tool that automates, facilitates and secures the AD administration, management and maintenance.
Improvements in Windows Server 2008
When AD was introduced in 2000 with the Microsoft Windows Server 2000, it revolutionized the network management and it became the most widely used network management Operating System that had almost all the basic features to handle the network requirements.
The access to the network from the client side became a completely controlled process that required a logon process from the client and needed an authentication from the server. Initially, it was designed as an Access Control List (ACL) to lemmatize the access to the network resources. Though it was quite successful but it could not get the expected feedback from the users and as the times passed, a large number of modifications were desired to cope with new demands.
Microsoft Metadirectory Services and Certificate Services were both apart of the AD and were needed to bring them into a suitable scenario to make the best use of them.
Now and Here
To bring a better integration with other network security modules, Microsoft Windows Server 2003 was introduced in 2003. Collaboration was created between the Certificate Services and the Active Directory. MIIS (Microsoft Identity Integration Server) replaced MMS(Microsoft Metadirectory Services) to integrate with other directories. Windows Rights Management Services and Authorization Manager were additionally added to the Windows 2003 Server for improved performance.
To implement a role-based access control, Authorization Manager was employed. It enabled the administrators to implement group permissions according to the job role. In this way, the users can be associated with compound job roles simultaneously.
Using RMS, the administrator gets the ability to allocate resources by the usage policies that hold fast to all information protection laws.
Windows Server 2003 had two more additional features meant to enhance the performance: ADAM (Active Directory Application Mode) and ADFS (Active Directory Federation Services in its second revision.
ADFS facilitated the controlled access to the web through a single sign-on authentication by creating a single session that allows the user to access multiple web applications on the same session.
The purpose of introducing ADAM was to create a feature through which directory based applications could benefit AD access control without making use of a domain controller or a real domain.
Windows Server 2008
Continuing the addition of more sophisticated features, Windows Server 2008 has emerged as the most equipped AD to fulfill almost all types of needs that one can expect from a DNS. Active Directory in Windows Server 2008 has the following features that make it more demanding:
Active Directory Domain Services (AD DS)
Read-only domain controllers (RODC)
Active Directory Lightweight Directory Services (AD LDS)
Active Directory Domain Services (AD DS)
Online certificate status protocol (OCSP) support
Active Directory Rights Management Services (AD RMS)
Active Directory Federation Services (AD FS)
Active Directory Certificate Services (AD CS)
Active Directory Lightweight Directory Services (AD LDS)
Enterprise PKI (PKIView)
Restart able AD DS
CAPI2 Diagnostics
Federation trust import/export support
Network device enrollment support
Auditing enhancements
Some tips to secure DNS:
1. Using DNS forwarders
DNS forwarders give you the advantage of performing your DNS queries on the behalf of some other DNS server. This is a performance oriented operation that reduces the processing burden of your DNS server by executing the DNS queries from some other DNS server and hence taking the advantage of larger DNS cache.
2. Using caching-only DNS servers
A caching-only DNS server does not rely on DNS domains. It can use forwarders or can perform recursions only. On receiving a response, the result is cached and the answer is returned to the system that issued the DNS query to this caching-only DNS server.
3. Using DNS advertisers
This type of DNS server works as an assistant to the DNS server for which it is authoritative to resolve the queries. Its use inhibits the DNS server from answering the queries for domains for which it is not authoritative hence reducing its burdens.
4. Using DNS resolvers
This is a dedicated server and is bound to resolve the internet host names only. It can resolve the domains for the DNS server using recursions. A DNS resolver can be made available to both the internal and external users to adopt the safest alternative to the DNS servers that are out of span of your control.
5. Protecting from cache pollution
When a DNS cache is polluted, the DNS server directs the user requests to malicious sites. Windows Server 2003 and Windows Server 20008 have a built-in feature of clearing the cache pollution where as you can configure the Windows Server 2000 for this action as well. In Windows Server 2003 and 2008, you can enable this feature from the Properties dialog box by clicking the Advanced tab and selecting the ‘Prevent Cache Pollution’ and then restarting the DNS server.
6. Enabling DDNS for secure connections only
A secure connection helps you reducing the malicious DNS updates while performing dynamic updates for the DNS servers using DHCP. This cannot be achieved without configuring the Active Directory zones to require secure dynamic updates.