Misc Security
I am receiving an error message which you can see at the below image. I am not able to uninstall and install Norton Antivirus. I need assistance to solve this .
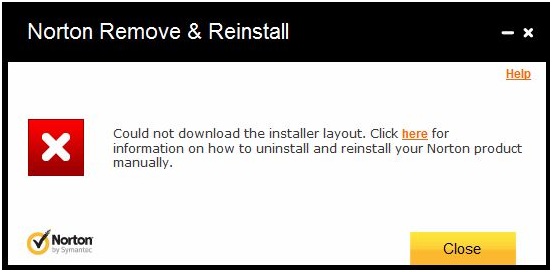
- 1575 views
- 1 answers
- 0 votes
Hi all experts,
I have just downloaded registered version Norton security antivirus for my laptop. This antivirus is working too good as compare with other Antivirus, but the problem is Norton utilities removes roccat files from the system. Can anyone educate me how to control or resolve this problem, will this create any problem to my system speed.
- 761 views
- 2 answers
- 0 votes
Hi,
I am trying to transfer Apache SSL Windows 2003 to Win2008R2 servers using WebLogic 10.3.5. But I am getting configuration errors. First hand information I got from the internet is that Win2003 servers are based on a 32bit version whereas Win2008R2 machines are 64bit version. So I downloaded the 64 bit version apache from ApacheLounge but I am getting error when I run httpd -t command, saying not a valid Win32 application.
Please solve my problem. Thanks
- 741 views
- 1 answers
- 0 votes
Can I decrypt a password using the rainbow tables and remove salt from the encrytped string? I know MD5 is one way but is it possible to decrypt salt md5 hash?
- 865 views
- 1 answers
- 0 votes
Dear All,
I want to know about Screen Pattern Locks. How does it work for a PC? Is it something similar to screen locks of iPhone? I need to find screen pattern lock for Windows XP. Can anyone help me?
- 761 views
- 1 answers
- 0 votes
I have been working with network application for security of my company purpose but recently I realized that it having some failures which used to result in data leaking and data loss which going to be a big threat for me now I want a type of protector tool which can configure data security function which can Detects and restricts use of devices plugged into your computers by type, model or even specific serial number as automatically search configuration protector type and deploy according to it ?
- 609 views
- 1 answers
- 1 votes
My brother installed Kaspersky Anti Virus to scan my file on my computer.
However, I find it very difficult and not very user friendly as I was more used to using Norton.
He says that it is a very good anti virus software and guarantees that I would have more protection on my computer.
I'd like to get some feedback regarding this software.
Is Kaspersky Anti Virus a good software to scan my file?
- 927 views
- 1 answers
- 0 votes
Hi guys,
My question focuses on how to generate a security key using the aes256 file tool, I also would like to know if it is possible to crypt any file with such a tool.
Are there any restrictions with respect to different operating system ?
Thank you.
- 876 views
- 1 answers
- 0 votes
I am using Windows Server 2008 and Windows XP in Client systems, I would like to have software that will help me to lock Client screen from Server, Please suggest me the better free Software.
- 768 views
- 2 answers
- 0 votes
Dear Experts,
I am going through a problem with my AVG 2012 registered version. I am using Windows XP. When AVG starts its automatic scheduled update, avg turns off while updating which may create harm to my PC if I am downloading or exchanging data with any other PC. Please guide me how to keep it on during update.
- 710 views
- 3 answers
- 0 votes











