Security
I get an occasional email error message when sending an email, saying "Email Error 421 – could not send – try again later."
- 1296 views
- 2 answers
- 0 votes
Zip files have some variation such as 7zip, winrar etc. I have some .rar files which I want to protect with password, but I haven’t any idea about password protection.
How can I protect the important files for sharing?
- 866 views
- 1 answers
- 0 votes
Hi All,
How Computer Forensics Works an insight will help.
Why do we call this Forensics and what can people do in computers 🙂
Thanks in advance
- 851 views
- 1 answers
- 0 votes
It is best practice that before you switch on to any network, the services which are not required should be disabled. It provides the more hole creation. If more holes are created, will the system be more secure? How can we disable service for Linux?
- 767 views
- 1 answers
- 0 votes
| In Unix Security, Privilege, Shared and Super accounts both can access the most sensitive data, yet since Privilege is the most powerful, is there any sufficient auditing which makes it easy to track down problems and make sure that Administrators only do the role they are going to perform? |
- 852 views
- 1 answers
- 1 votes
I am testing EERM and have configured a policy that protects the entire USB drive and makes it read only if not protected. Everything works as fine except that it appears Autorun may be required to be enabled on a machine with EEFF (including EERM) installed.
I asked because, with autorun enabled, inserting the USB drive produces a password prompt and if the correct password is entered, everything is ok. If Cancel is clicked at the password prompt, the drive looks just like it does on a machine without EEFF installed. However, attempting to execute MfeEERM.exe on the machine with EEFF installed produces the following error.
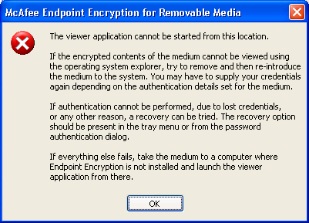
McAfee Endpoint Encryption for Removable Media
- 5903 views
- 1 answers
- 0 votes
How can you be sure that storing your personal data on cloud based services can be safe against internet fraud? Are there ways for users to protect and control their personal data on a cloud based model? What are the most common cloud security issues you encountered? Replies will be highly appreciated. Thank You!
- 1024 views
- 1 answers
- 0 votes
I always save and collect photo and video "special and personal", it will be a dilemma between "must" save your collection, or delete them. I certainly do not want a time when families, children, friends or relatives to your work access accidentally discovered that my collection. Then how do i protect the collection folder, so it is not easy even can not be accessed by someone other than me ?
- 672 views
- 2 answers
- 0 votes
I have lots of network computers and I have to put security using my smart card reader ICE 5700 Plus, I used it on my Windows 7 Client and it works fine when I installed it. When I logon to the system, it asked me about certificate? Where do I find the certificate asked by the computer system?
- 804 views
- 1 answers
- 0 votes
Hello All,
I want to customize my logon password on my laptop in the sense that instead of the normal enter password, I want to ASK A QUESTION and the answer to the question will be the logon password. Suggestions anyone?
- 984 views
- 3 answers
- 0 votes











