How To Configure SonicWALL SSL VPN Setup With Overlapping Subnet

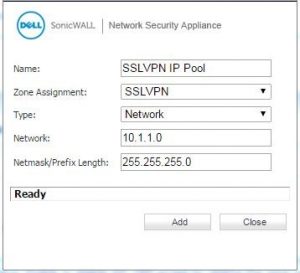
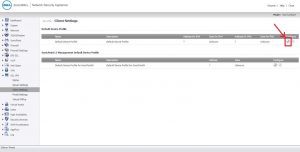
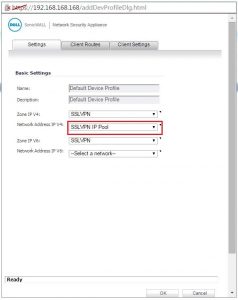
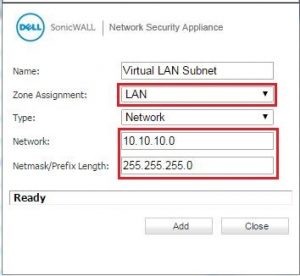
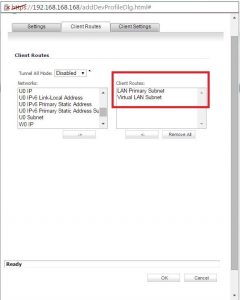
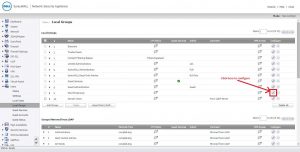
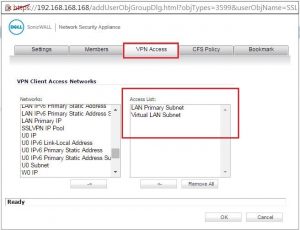
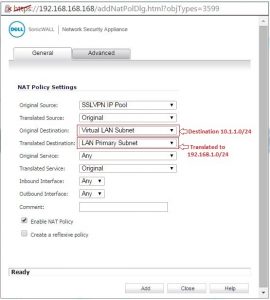
I am not able to access SonicWall LAN resources. I don’t know any possible way by which I can access them. I know the cause of such a problem is due to overlapping subnets. Can anyone help me to configure SonicWALL SSL VPN setup to eliminate this problem?