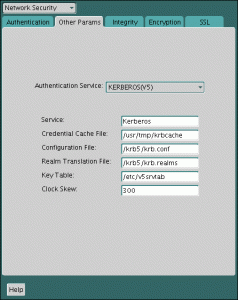
Implementations Of Kerberos In Network Security Protocol

What is Kerberos protocol? How is Kerberos network security used? From where is the word Kerberos derived? Who developed the Kerberos protocol?