Public Key Encryption example description

When I was searching about the Public Key Encryption I found this diagram that explains about the Public Key Encryption process.
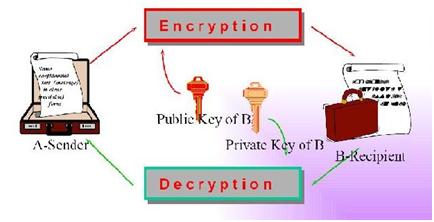
But I cannot understand what it will describe. So someone please describe me what is explaining from this diagram.













