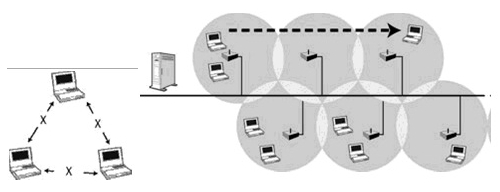
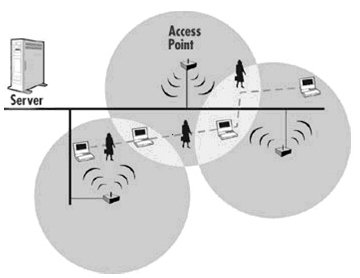
WLAN Security Threats caused by unauthorized actions

Nowadays, wireless LAN is widely used, as it is very convenient for building a network easily, without managing physical cables.
So please, I want information as to what unauthorized actions might be committed easily, in a wireless LAN environment.
Thanks.