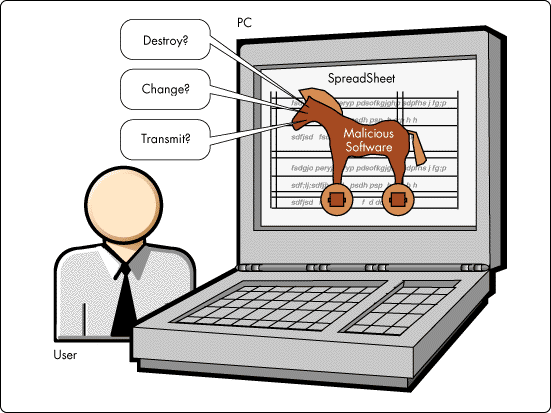
Let’s be aware of Trojan horses which enter your pc silently
Have you ever lost your valuable data due to a Trojan horse attack?
Then you might have an experience how silently it came in to your pc. Most of the time these infected files come in to your pc disguising in an innocent application like a small game or software.

- Some Trojan horses monitor everything that we type including credit card information and send them to the creator by using our pc’s internet.
- It is proved that this virus contains in JPEG, MPEG and exe files than other files.
- To avoid Trojan horse attacks you have to run an up-to-date firewall.
- If there are files like image.jpeg.exe that means it’s a Trojan horse. Under default conditions it’s shown to the user as a non-harmful image file but the real extension of the file is .exe