Recent posts

Intel vs. Amd processors Both AMD and Intel processors possess certain good qualities and they continue to dominate the market as the manufacturers remain consistent in introducing new, even better and competitive technologies. Main categories and technical details of Intel and AMD processors Intel There are three main categories in the Intel...
Read more

ICT- Overview ICT which refers as the Information and Communications Technology is basically a synonym that is being used for Information Technology in the modern times, but formerly, it is commonly used as the fact that it emphasizes on the role of communications in terms of the Information Technology...
Read more

What is the ExMerge utility? ExMerge It all started with Windows 95 windows messaging which was named as Microsoft Exchange. An e-mail client was also included separately back then. Prime focus of the software: Efficient communication through e-mail. Then came Windows 98 and the Microsoft Exchange...
Read more

Exchange Vs. Lotus Introduction Gargantuan market leaders battle the specter of consumer doubt. Genuine effort that results in superb products rightfully occupies the lion's share of the market. But often, consumers still wonder, “Am I being short-changed? Is this the best? I deserve the best, don't I?" Microsoft products dominate the...
Read more
INTERNET CONNECTIVITY: BRIDGING PEOPLE The proliferation of internet usage these days can be found anytime, anywhere, static or mobile. The surfers are utilizing different ways to connect to the internet according to their needs. There are four ways to connect to the internet: A. ANALOG. It is...
Read more

Blue Coat Systems Amazing Solutions For any business organization, security is a must-have in their day to day life. Security in computer industries includes the information asset protection through the utilization of technology, training, and processes. Various businesses that provide security in different areas of the industry are burgeoning.
Read more
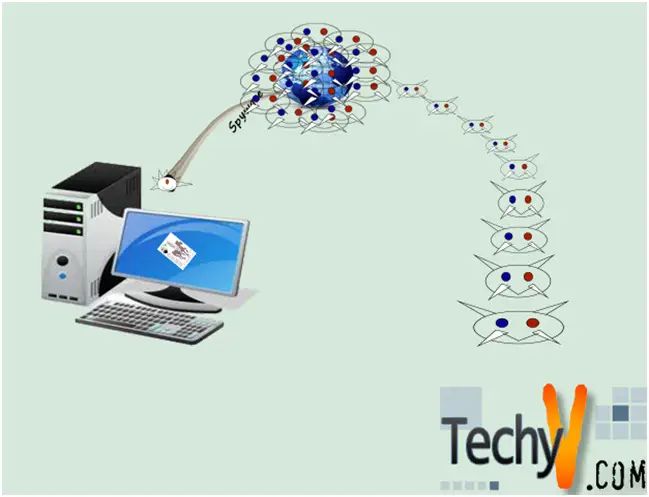
What is a Spyware? Spyware and Adware collect system or personal information from your computer without your knowledge and report about that data to the perpetrator. Information collected can be personal information, email address, buying habits, website visits and also financial account information and password details. The information can be used...
Read more

What effects will cloud computing have on the computer industry What effects will cloud computing have on the computer industry. Who will feel either positive or negative effects? Cloud computing has provided the much awaited computer solution for all. It provides freedom for corporations and individuals to invest their stakes in more business oriented opportunities than...
Read more
Virtual Private Network (VPN), More Secured Less Cost Recently, business world enhanced the productivity of their workers simply by establishing a constant contact with them. As long as there is an open access to the company’s data even though you are on the travel, deadlines can be still be...
Read more

Advanced ip scanner and Advanced port scanner Advanced ip scanner: As the name indicates IP scanner is used to scan IP addresses. Advanced IP scanner is a user friendly, robust and fast IP scanner available for windows operating system. The Advanced IP scanner is used to track different types...
Read more










