Recent posts
I have windows 2003 ad setup in my office and do regular checks on disabled users and some other general checks by using the search filter methods .
I need an expert opinion about this. Kindly suggest your best advice. What's the best option for SAN? What are the best storage preferred by small scale companies?
Read more
Hi Experts,
This is my 2nd question here and the first was an awesome solution. So trying to put across my issues to you guys.
I have a file server that's windows 2003 and it’s an old box with 100's of shares in them many are for team users where multiple...
Read more
Hi,
When i try to disk defragment i get this error message "Disk Defragmenter Could Not Start".
Anyone knows of a fix for this issue.
I have Windows XP
and also some times the attached error

Microsoft Management Console
Snap-in failed to initialize.
Name:<unknown>
CLSID:{43668E21-2636-11D1-A1CE-0080C88593A5}
Thanks in advance
Deshpande
Read more
I have 300+ machines on my network. The problem is when my staff tries to log back in, they were unable to get an IP address. Checking on the AD server which I used to serve as a DHCP, it was up and running actively.
But running the ipconfig command...
Read more
Hi,
Deleted some user accounts by mistake in Active directory. Can you help retrieving them. I have another question posted in this site about a desktop issue as well.
Thanks.
Magi
Read more
I get this error
svchost.exe -- application error the instruction at "0x745f2780" reference memory at "0x00000000". the memory could not be 'read'
when closed the error box the windows restarts and when left it alone it stays On.
Can anyone help me with a solution. Googling did not help much
Read more
Hi,
For few users we are getting error like
Windows cannot connect to the domain, either because the domain controller is down or otherwise unavailable, or because your computer account was not found.
Waiting for your reply.
Cheers, Bipin
Read more
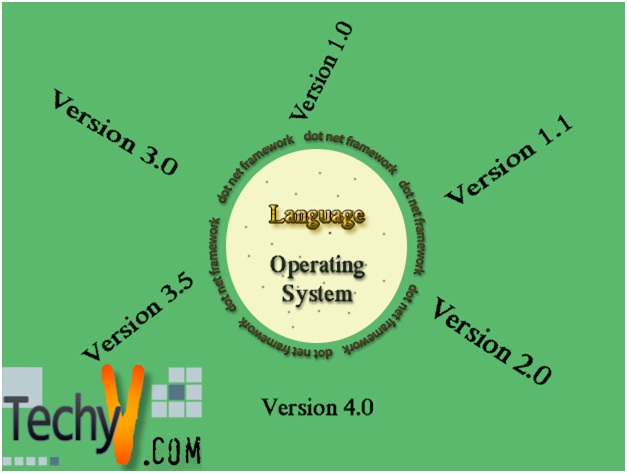
Microsoft .net Framework Microsoft .net framework is a framework application which provides the bridging for programming languages and windows operating system. It is the common layer which includes libraries, definitions, code compatibility, language compatibility and much more. It is installable on every Microsoft Windows Operation System. Microsoft .net framework allows...
Read more

From Paper to 3TB HDD For several years, paper was utilized as the most important storage medium in the history of computer systems. Picture a life of punching holes into paper tapes or punch cards to record a program and data in your computer. Imagine yourself...
Read more










