Recent posts
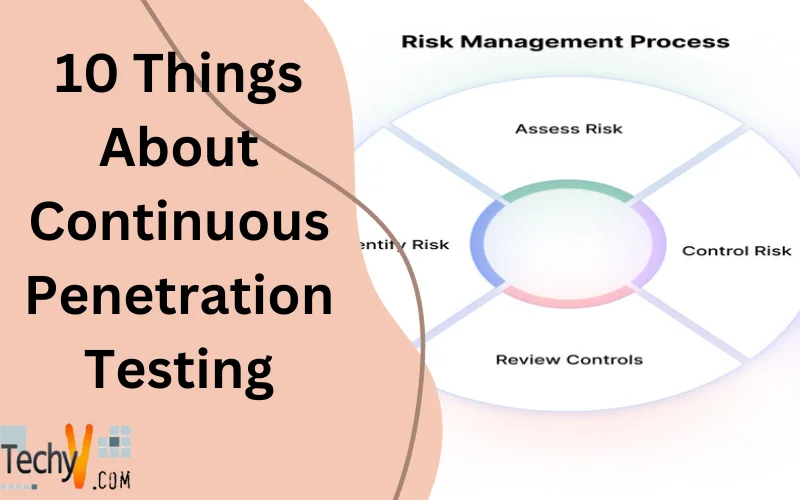
What Is Continuous Penetration Testing? Conducting a penetration test at least periodically means continually accessing your security posture. Continuous penetration testing is a subset of ethical hacking devoted to securing the security posture of your business. It frequently shows the flaws exploited by hackers to breach your management IT bubble....
Read more
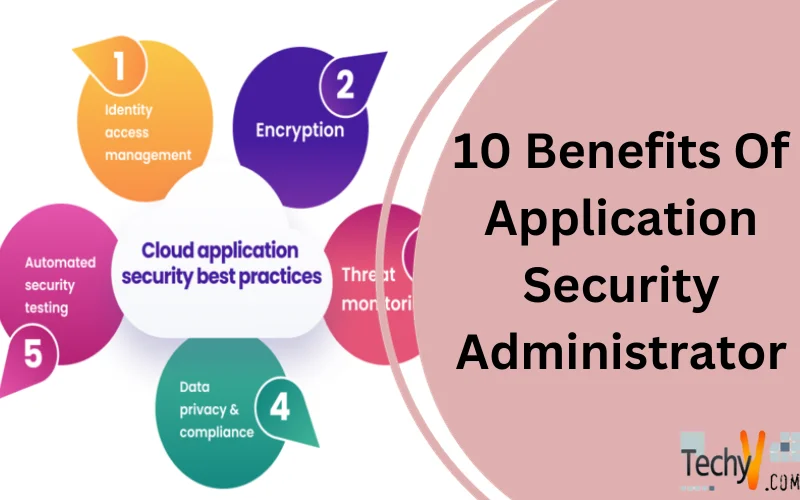
What Is An Application Security Administrator? Application Security is developing, deploying, and testing an application’s security features to avoid security loopholes from hazards. It defines the security calculates needs at the application stage to protect the application code and data from cyberattacks. Application security involves software, hardware, and processes to reduce...
Read more

IT Service Management (ITSM) frameworks provide structured guidance to manage the delivery of IT services end-to-end while optimizing costs. However, simply implementing the ITIL guidelines or processes from your chosen framework is not enough to guarantee ITSM success. Organizations need to embrace core ITSM best practices across people, process,...
Read more
Artificial intelligence infuses modern customer service, empowering companies to strengthen support capabilities. Integrating AI optimizes operations, capturing unified customer data, and applying intelligent automation for efficient issue resolution. As customers expect personalized, seamless interactions across channels, AI-enabled platforms directly enhance satisfaction. Companies should evaluate top solutions to determine ideal...
Read more

Serverless computing has transformed the way companies build and deploy applications by allowing them to run backend code without managing any servers. This enables greater agility, reduced costs, and auto-scaling capabilities. As the market leader, Amazon Web Services' (AWS) Lambda service drives most of this serverless growth given its...
Read more

Data breaches from human error and cyber attacks have unfortunately become commonplace, with serious consequences for companies in terms of financial penalties, loss of customer trust, and impacts on overall business operations. Implementing solutions to protect sensitive data through proper classification, monitoring, and encryption is no longer optional in...
Read more

As the fuel that powers data-driven decision-making, high-quality data is an invaluable asset for modern enterprises. However, with data volumes growing at an exponential pace across systems and silos, organizations struggle to maintain data health. Flawed data ripples across operational efficiency, revenue leakage, compliance risks, and customer experiences. Investing...
Read more

Privileged Access Management(PAM) as a solution offers security and protects an organization from cybercrimes by rigorously monitoring and preventing unauthorized access to business-critical resources. Using a smart combination of human, processes, and technology gives an idea of who all are using the privileged accounts and their login activities. Privileged...
Read more

Often, drivers diving underwater find it difficult to communicate due to radio waves. Sometimes, the divers use sign language with each other for communication. But with the introduction of underwater walkie-talkies, divers can communicate underwater over long distances by sending radio messages along the water surfaces. A good quality...
Read more

Artificial Intelligence has emerged as one of the positive innovations made in recent years. More than 50% of companies have started adopting AI for their business operations. Utilizing AI technology has helped businesses worldwide to improve their efficiency and productivity. The world is moving quickly, and in every second,...
Read more










