Recent posts

What Are Composable Platforms? Composability is manufacturing software using “building blocks” consisting of interchangeable, integrative company capabilities. At their most primary stage, composable platforms are what non-technical teams and people use to collect and gather those building blocks to generate their full-blown software solutions, all without always having to write...
Read more
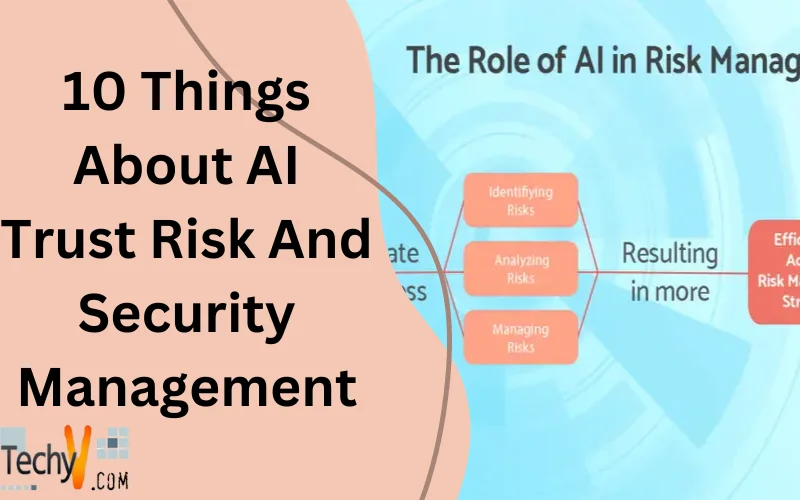
What Is AI Trust Risk And Security Management? Artificial Intelligence (AI) has experienced quick growth, allowing companies to forecast better, automate procedures, and make decisions more rapidly and correctly. This power of AI also prompts potential risks, such as data leakage, tampering, and malicious attacks. Businesses must go behind standard...
Read more

What Is An Autonomous System? An Autonomous System (AS) in networking is a gathering of one or more connected internet protocol (IP) preface with clearly defined routing protocols that govern how the autonomous system covers routing information with other autonomous systems. An independent system can be considered a connected group...
Read more
What Is Supercharge Sustainability? Super Sustainability is the concept of accelerating or increasing efforts and operational goals to promote sustainability. It implicitly goes on behind incremental enhancements and embraces transferring changes that have a profound and lasting effect on surroundings, and social and economic sustainability. Supercharging Sustainability includes the execution of...
Read more

What Is Biometric Authentication? Biometric authentication refers to strategies of using biology like fingerprints, eyes, voice, and even interior features to confirm the recognition of individuals. Biometrics are better than standard passwords used for authentication because they verify exactly what you recognize through inherent biological features. Password theft methods such...
Read more
What Is API-driven Productivity? API-driven productivity is the procedure of designing and manufacturing APIs first, then making the rest of an application around them. API-driven development is distinct from standard development strategies. Those usually involve API design and execution as one point on the development timeline, and it does not...
Read more

What Is Applied Observability? Applied observability is a globally popular business practice where you use several tools and methods to draw insights from the actions and performance of a given system. The subject of observation is frequently a complex operational system like business apps, IT networks, cloud infrastructure, or any...
Read more

Gaining a detailed understanding of website visitor behavior provides crucial insights that empower product teams to incrementally optimize and refine digital experiences, enable marketing organizations to precisely optimize go-to-market motions across engagement channels, and equip business leaders to make smarter data-informed strategic decisions leading to substantially improved online conversion...
Read more

Selecting the optimal database solution warrants careful analysis depending on business requirements, as the data layer forms a foundational component across enterprise systems. Vendors offer divergent capabilities targeting different use cases - whether transactional, analytical, or hybrid workloads. As part of regular evaluation cycles, DBAs need to thoroughly assess...
Read more

With over 60% of website traffic now originating from mobile devices, having a mobile-friendly website is no longer just an option, it is a necessity for any business looking to effectively reach today's on-the-go consumers. However, creating an optimized mobile experience requires more than just squeezing your desktop site...
Read more










