Recent posts
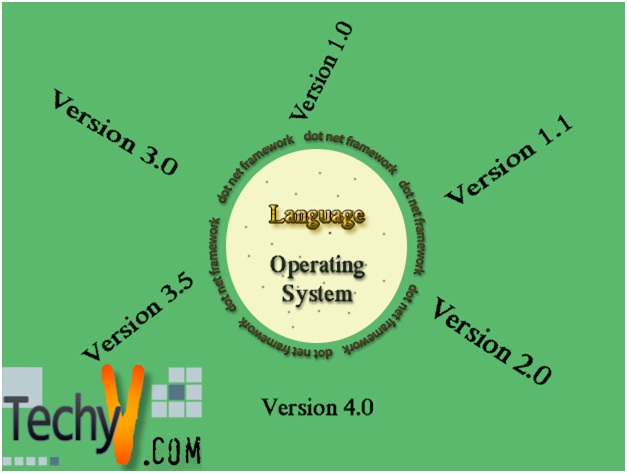
Microsoft .net Framework Microsoft .net framework is a framework application which provides the bridging for programming languages and windows operating system. It is the common layer which includes libraries, definitions, code compatibility, language compatibility and much more. It is installable on every Microsoft Windows Operation System. Microsoft .net framework allows...
Read more

From Paper to 3TB HDD For several years, paper was utilized as the most important storage medium in the history of computer systems. Picture a life of punching holes into paper tapes or punch cards to record a program and data in your computer. Imagine yourself...
Read more
Lync server: HISTORY Microsoft Office Live Communications Server was initially launched on December 29, 2003 to replace the Exchange Instant Messenger service included in Exchange 2000, which was withdrawn from all the features of Exchange 2003. Dealers, including Exchange 2000 Software Assurance are entitled...
Read more

Introduction to Computer & IT Insecurity Computer security and IT security are terms associated with the protection of computer software, hardware, and the network systems from the hazards of external attacks from virus, cracking, hacking, etc. In fact, the security measures and policies aim at safeguarding or protecting the...
Read more

Ethical Hacking and its Difference to Malicious Hacking Ethical Hacking is also often termed as Intrusion, Penetration Testing, Tiger Teaming, Sneaking, or Red Teaming. The methodologies used for ethical hacking are similar to those used for malicious hacking. The only difference between the two is the former uses the...
Read more
Computer Network’s Security Systems Penetration Penetration refers to a successful, but an unauthorized breach of security perimeter of a computer system. Penetration Testing is done as a part of ethical infiltration, wherein the computer network’s security systems are evaluated thoroughly by simulating attacks from malevolent sources, also called the...
Read more

Vulnerability with regards to computer security Vulnerability, with regards to computer security, refers to weakness in the computer system or network that enables an attacker to make unauthorized access into the system and affect its information assurance. Any venerability is nothing, but an intersection of 3 basic...
Read more
CSharp Language: Its History and Uses The symbol of programming language that will be discussed later was rooted on the note of music which is the see sharp note. The sharp signifies a pitch that is higher in half-step. Due also to the restrictions of the computer display and...
Read more

Performance of browsers: A short Study Firefox 3.5: The most unique feature of Firefox is its simplicity. Users will be excited with so many features like, customized tools and features, all types of add-ons, Smart Location Bar, an Instant Web Site ID, Improved Tabbed Browsing, an integrated search engine, Location-Awareness feature, Spell...
Read more

All about Exchange Server 2003 Tools – Top 20 Tools You might have heard of the exchange server 2003 tools, which are in abundance for several different purposes, but perhaps, you’re not yet aware of their unique features, enhancements, how they work and their compatibility with other exchange servers...
Read more











