Recent posts
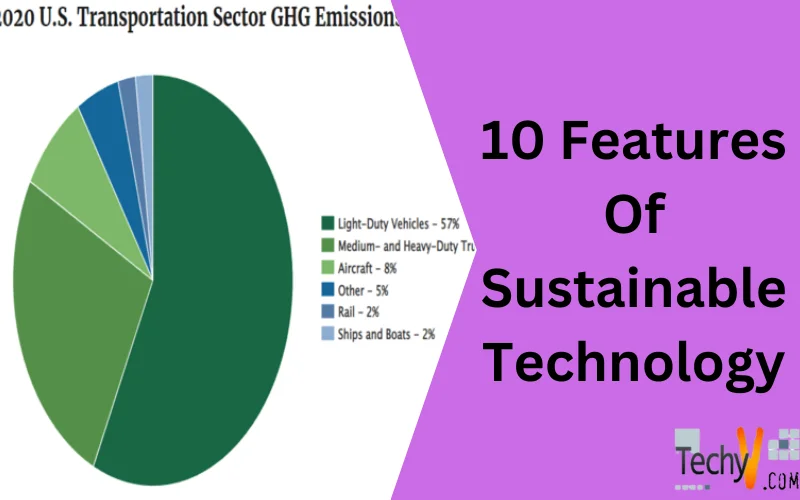
What Is Sustainable Technology? Sustainable technology is a broad term that means technologies that are considered natural resources and inspire the development of society and communities. The innovation’s goals are to lessen ecological and environmental risks dramatically risks and to offer sustainable products. The term sustainable technology is used in...
Read more
What Is A Data Fabric? Data Fabric is an end-to-end data inclusion and organization solution comprising architecture, data management and inclusion software, and shared data that helps management organize their data. A data fabric provides a united, persistent user experience and access to data for any member of management worldwide...
Read more

What Are Autonomous Systems? Autonomous Systems, such as self-driving automobiles and some robots, are used without the intervention of humans. An autonomous system can achieve a specific set of goals in an alternate environment, collecting information about the environment and working for an extended period without human intervention or control....
Read more
What Is Continuous Penetration Testing? Conducting a penetration test at least periodically means continually accessing your security posture. Continuous penetration testing is a subset of ethical hacking devoted to securing the security posture of your business. It frequently shows the flaws exploited by hackers to breach your management IT bubble....
Read more
What Is An Application Security Administrator? Application Security is developing, deploying, and testing an application’s security features to avoid security loopholes from hazards. It defines the security calculates needs at the application stage to protect the application code and data from cyberattacks. Application security involves software, hardware, and processes to reduce...
Read more

IT Service Management (ITSM) frameworks provide structured guidance to manage the delivery of IT services end-to-end while optimizing costs. However, simply implementing the ITIL guidelines or processes from your chosen framework is not enough to guarantee ITSM success. Organizations need to embrace core ITSM best practices across people, process,...
Read more
Artificial intelligence infuses modern customer service, empowering companies to strengthen support capabilities. Integrating AI optimizes operations, capturing unified customer data, and applying intelligent automation for efficient issue resolution. As customers expect personalized, seamless interactions across channels, AI-enabled platforms directly enhance satisfaction. Companies should evaluate top solutions to determine ideal...
Read more

Serverless computing has transformed the way companies build and deploy applications by allowing them to run backend code without managing any servers. This enables greater agility, reduced costs, and auto-scaling capabilities. As the market leader, Amazon Web Services' (AWS) Lambda service drives most of this serverless growth given its...
Read more

Data breaches from human error and cyber attacks have unfortunately become commonplace, with serious consequences for companies in terms of financial penalties, loss of customer trust, and impacts on overall business operations. Implementing solutions to protect sensitive data through proper classification, monitoring, and encryption is no longer optional in...
Read more

As the fuel that powers data-driven decision-making, high-quality data is an invaluable asset for modern enterprises. However, with data volumes growing at an exponential pace across systems and silos, organizations struggle to maintain data health. Flawed data ripples across operational efficiency, revenue leakage, compliance risks, and customer experiences. Investing...
Read more










